
Harness offers robust features for security and compliance, including strong authentication, role-based access control, audit trails, approval stages, and policy-as-code governance, ensuring organizations meet stringent security standards.
At Harness, we’re not only busy building a software delivery platform for the world’s software developers, we are also our own customer and continue to “dogfood”(https://en.wikipedia.org/wiki/Eating_your_own_dog_food) our products by using them internally.
While this allows us to have a world class engineering organization with modern software development capabilities, it also means that WE rely on the platform to be built with robust security features in order for our company to meet the same security and compliance requirements (SOC, ISO, etc) that apply to the vast majority of our customers.
Harness’ own Governance, Risk, and Compliance team (GRC) is responsible for partnering with the broader engineering organization to identify, design, and implement the required controls within our Harness Platform accounts, in order to maintain a robust security environment and meet our compliance requirements.
Here are the top 5 Harness Platform features we use extensively at Harness to enhance our security & compliance posture:
1. Strong Authentication
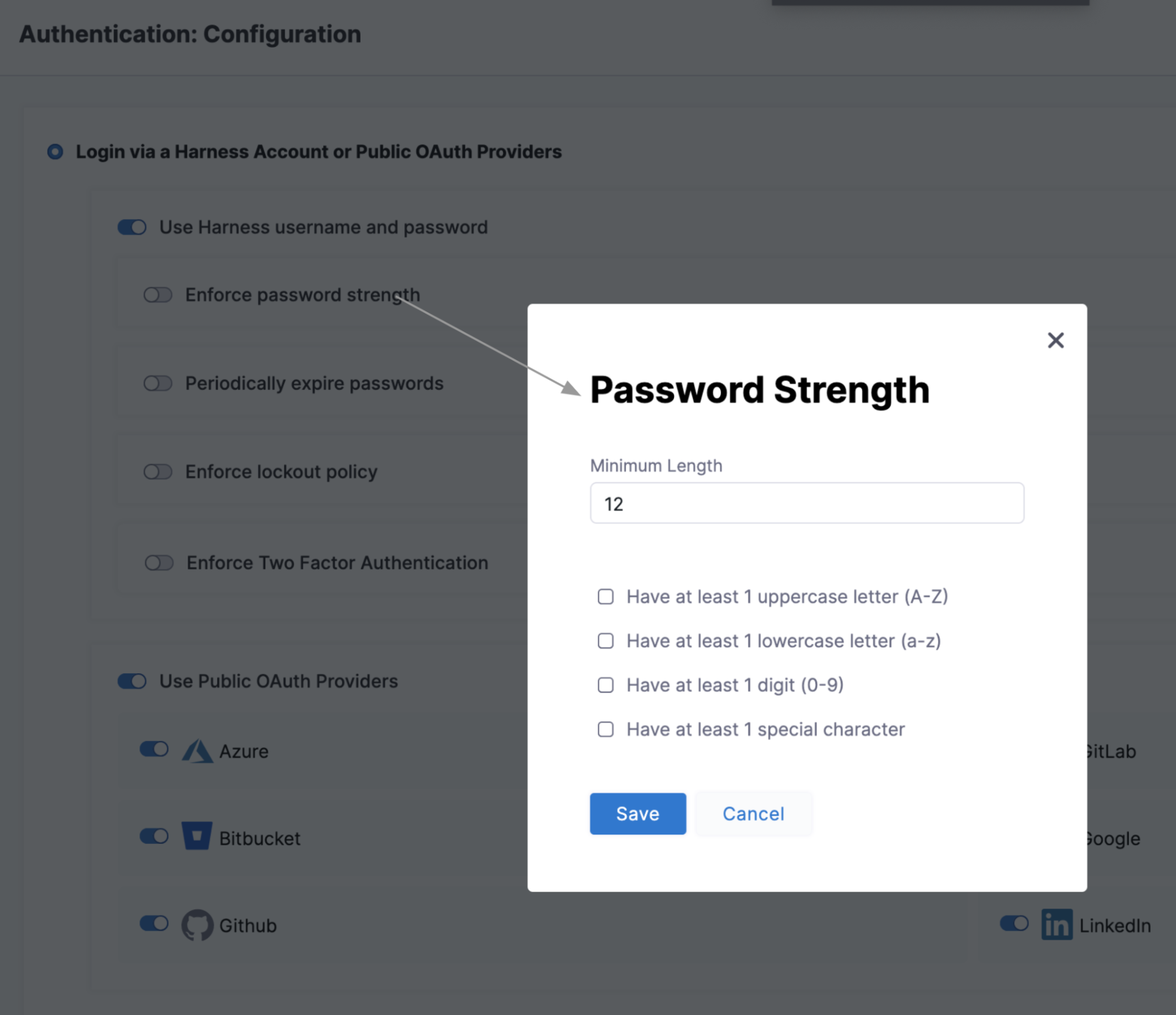
The Harness Platform supports the configuration of strong authentication requirements which is a key control in many compliance frameworks. Customers can leverage the following mechanisms to authenticate users1:
- Public OAuth Providers
- SAML
- LDAP
- Configurable Local Authentication

If Local Authentication is used, administrators can configure additional password parameters such as Password Strength, Expiration, Lockout Policy, and Two Factor Authentication to comply with organization policies.
The Harness Platform can also restrict email domains, manage IP allowlists, and enforce session inactivity timeouts to further enhance security around access and session management.
1Harness Authentication Overview
Related Compliance Standards and Framework
- AICPA Trust Services Criteria
— CC6.1 -The entity implements logical access security software, infrastructure, and architectures over protected information assets to protect them from security events to meet the entity's objectives.
- ISO 27001:2013
— A9.2.3 - The allocation and use of privileged access rights should be restricted and controlled.
— A9.2.4 - The allocation of secret authentication information should be controlled through a formal management process.
— A.9.3.1 - Users should be required to follow the organization's practices in the use of secret authentication information.
— A9.4.3 - Password management systems should be interactive and should ensure quality passwords.
- ISO 27001:2022
— 8.2 - The allocation and use of privileged access rights should be restricted and managed.
— 5.17 - Allocation and management of authentication information should be controlled by a management process, including advising personnel of appropriate handling of authentication information.
2. Configurable Role Based Access Controls
Protecting sensitive data is essential for a strong infosec posture. Therefore, the Harness Platform can be configured to control who has access to certain resources and what actions they can perform. Authorized users should only be able to perform actions that are associated with their role within an organization. Leveraging Role-Based Access Controls addresses the fundamental principles of security such as least privilege and the need for accountability.
The Harness Platform allows organizations to design an RBAC model2 with a hierarchical structure that can scope access to resources as broadly or as narrowly as required.
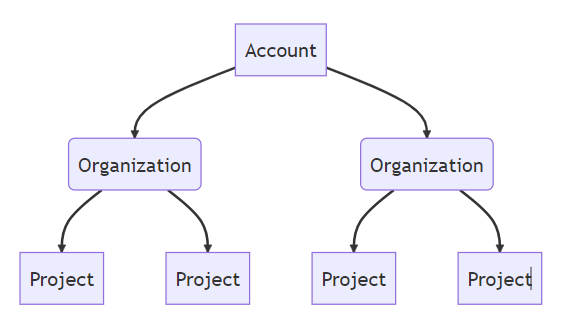
Additionally, custom roles and attribute-based access controls (ABAC) can be further leveraged to design even more limited fine-grained permissions across resources and actions.


The Harness Platform is also compatible with the open standard protocol System for Cross-Domain Identity Management (SCIM) for automating user provisioning and deprovisioning, supporting requirements for formal user registration, de-registration, role assignment, or change of access rights. Currently SCIM integration is supported with Okta, Microsoft Entra, and OneLogin.
Okta Example
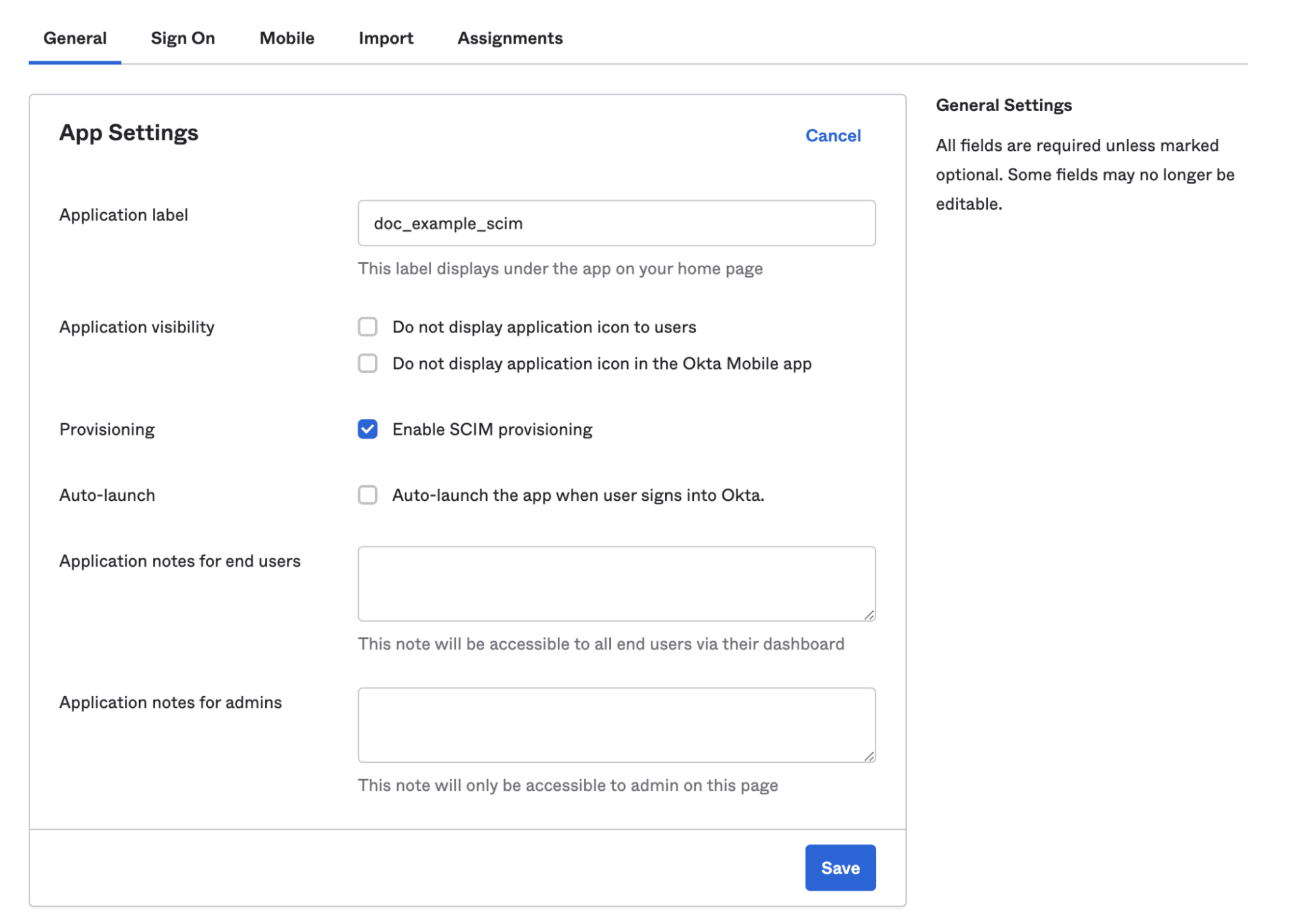
2https://developer.harness.io/docs/category/access-control-1
Related Compliance Standards and Framework
- AICPA Trust Services Criteria
— CC6.1 - The entity implements logical access security software, infrastructure, and architectures over protected information assets to protect them from security events to meet the entity's objectives.
— CC6.2 - Prior to issuing system credentials and granting system access, the entity registers and authorizes new internal and external users whose access is administered by the entity. For those users whose access is administered by the entity, user system credentials are removed when user access is no longer authorized.
— CC6.3 - The entity authorizes, modifies, or removes access to data, software, functions, and other protected information assets based on roles, responsibilities, or the system design and changes, giving consideration to the concepts of least privilege and segregation of duties, to meet the entity’s objectives.
- ISO 27001:2013
— A9.2.1 - A formal user registration and de-registration process should be implemented to enable assignment of access rights.
— A9.2.2 - A formal user access provisioning process should be implemented to assign or revoke access rights for all user types to all systems and services.
— A9.2.3 - The allocation and use of privileged access rights should be restricted and controlled.
- ISO 27001:2022
— 5.16 - The full lifecycle of identities should be managed.
— 5.18 - Access rights to information and other associated assets should be provisioned, reviewed, modified and removed in accordance with the organization’s topic-specific policy and rules on access control.
— 8.2 - The allocation and use of privileged access rights should be restricted and managed.
3. Out of the Box Audit Trail
The Harness Platform has a built-in audit trail3 that displays records for events that change the setup of a platform account.
The audit trail shows the date and time (Time), user who made the change (User), action taken (Action), resource affected (Resource), corresponding organization (Organization), corresponding project (Project), corresponding module (Module), and an event summary that shows the change via YAML.

Various filters can also be used to parse through the audit trail and focus on captured events within a specific time period for review such as unauthorized access or configuration changes.

Additionally, detailed pipeline execution histories are also captured, further tracking what was executed, when the execution took place, and who initiated the action. These executions can also be filtered similar to the Audit Trail for more detailed parsing and investigation.

At Harness, we use the audit trail and execution history internally when reviewing new user creation dates to support our external audit requests, as well as to validate when new releases are deployed to production to remediate pending library vulnerabilities.
3https://developer.harness.io/docs/platform/governance/audit-trail/
Related Compliance Standards and Framework
- AICPA Trust Services Criteria
— CC4.1 - COSO Principle 16: The entity selects, develops, and performs ongoing and/or separate evaluations to ascertain whether the components of internal control are present and functioning.
— CC7.2 - The entity monitors system components and the operation of those components for anomalies that are indicative of malicious acts, natural disasters, and errors affecting the entity's ability to meet its objectives; anomalies are analyzed to determine whether they represent security events.
- ISO 27001:2013
— A12.4.1 - Event logs recording user activities, exceptions, faults and information security events should be produced, kept and regularly reviewed.
— A12.4.3 - System administrator and system operator activities should be logged and the logs protected and regularly reviewed.
- ISO 27001:2022
— 8.15 - Logs that record activities, exceptions, faults and other relevant events should be produced, protected, stored and analyzed.
4. Approval Stages
In addition to ensuring only authorized users can perform certain actions, implementing Approval Stages4 in key pipelines can also provide additional authorization and notification controls within a pipeline execution. This helps to ensure that activities impacting critical systems and environments are appropriate.

A specific “Approvers” user group can be configured within the platform and assigned to the pipelines that require this step, allowing additional coverage or multiple approvals to be required for the stage to pass. Harness also prevents the user that initiated the pipeline from being able to approve this step in the process, which further enforces the principle of separation of duties.
Leveraging key configurable controls further strengthens the accountability of the change management process as well as the integrity of the environments and systems being impacted.
4https://developer.harness.io/docs/category/approvals-1
Related Compliance Standards and Framework
- AICPA Trust Services Criteria
— CC3.4 - COSO Principle 9: The entity identifies and assesses changes that could significantly impact the system of internal control.
— CC8.1 - The entity authorizes, designs, develops or acquires, configures, documents, tests, approves, and implements changes to infrastructure, data, software, and procedures to meet its objectives.
— CC6.8 - The entity implements controls to prevent or detect and act upon the introduction of unauthorized or malicious software to meet the entity’s objectives.
- ISO 27001:2013
— A12.1.2 - Changes to the organization, business processes, information processing facilities and systems that affect information security should be controlled.
— A14.2.2 - Changes to systems within the development lifecycle should be controlled by the use of formal change control procedures.
— A.14.2.3 - When operating platforms are changed, business critical applications should be reviewed and tested to ensure there is no adverse impact on organizational operations or security.
— A.14.2.4 - Modifications to software packages should be discouraged, limited to necessary changes and all changes should be strictly controlled.
- ISO 27001:2022
— 8.32 - Changes to information processing facilities and information systems should be subject to change management procedures.
5. Harness Policy-as-Code
Harness Platform governance is a Policy-as-Code5 approach based on the Open Policy Agent (OPA), an open-source policy engine that enables the definition and enforcement of policies across the platform. Users can define rules and constraints that can be applied to processes throughout the software delivery process, as well as specific entities.
Policies can be written and tested in the built-in policy editor and can be saved individually or with other policies as a Policy Set.
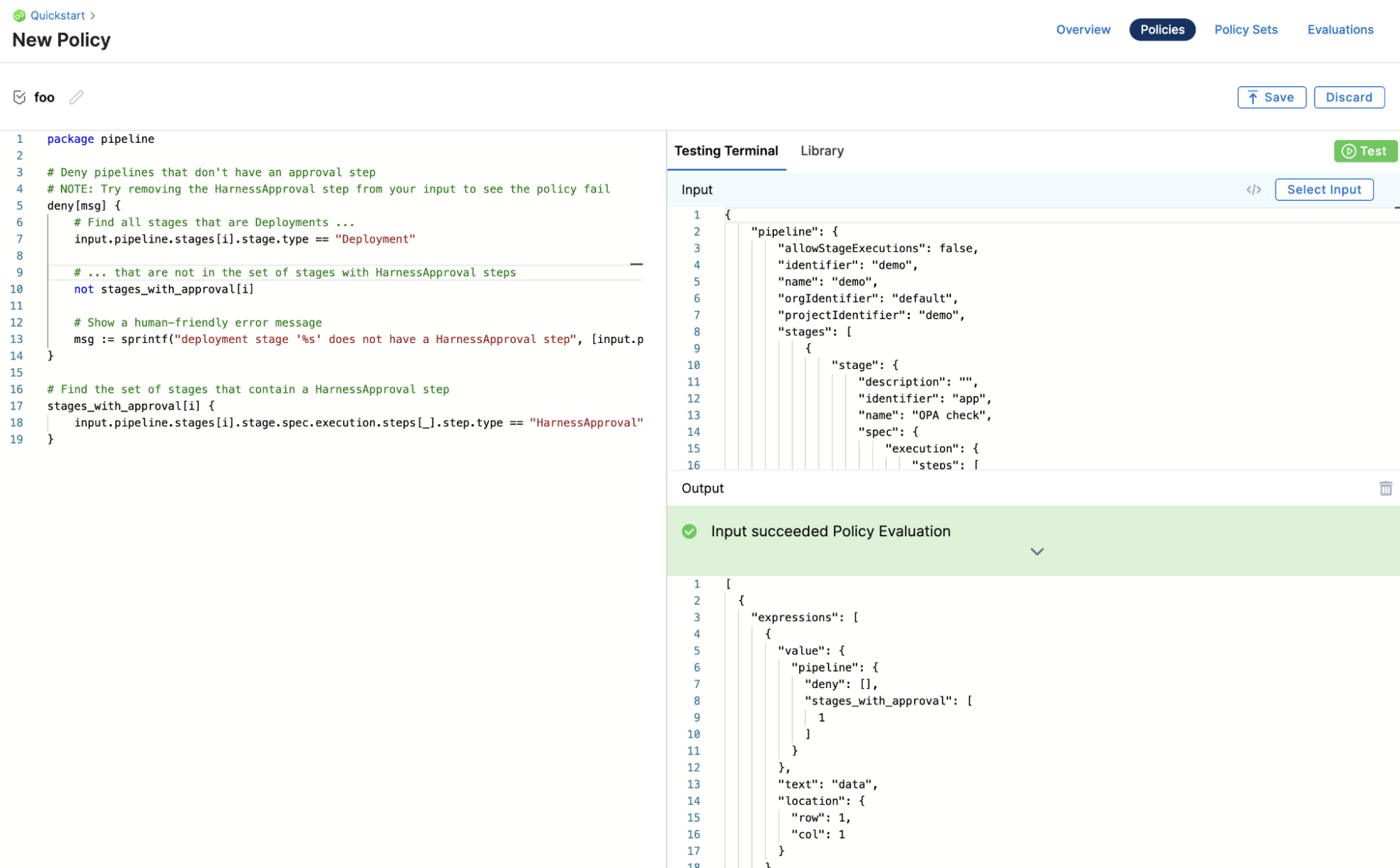
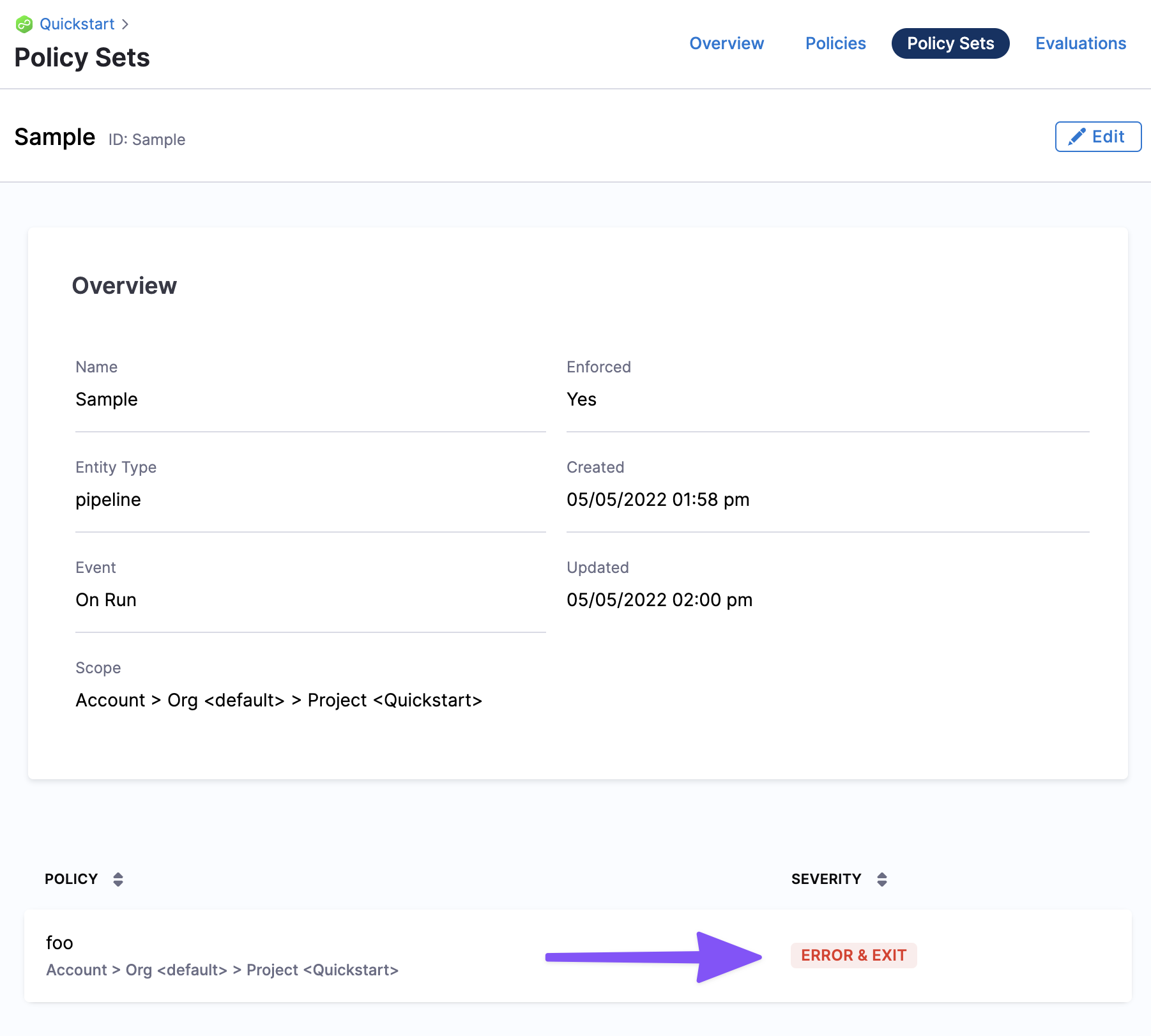
Policies and Policy Sets can be used to enforce compliance requirements and automated controls such as approval steps, restricting forbidden activities, enforcing deployment freezes, or blocking builds or deployments if Critical or High Vulnerabilities are identified during a scan within a pipeline.
Policy-as-Code governance within the Harness Platform can help Security and Compliance teams ensure automated and configurable controls continue to operate efficiently and effectively, reduce the risk of manual errors occurring, and enhance the security of development teams within their processes.
Related Compliance Standards and Framework
- AICPA TSC
— CC7.1 - To meet its objectives, the entity uses detection and monitoring procedures to identify (1) changes to configurations that result in the introduction of new vulnerabilities, and (2) susceptibilities to newly discovered vulnerabilities.
— CC8.1 - The entity authorizes, designs, develops or acquires, configures, documents, tests, approves, and implements changes to infrastructure, data, software, and procedures to meet its objectives.
- ISO 27001:2013
— A.14.1.1 - The information security related requirements should be included in the requirements for new information systems or enhancements to existing information systems.
- ISO 27001:2022
— 5.8 - Information security should be integrated into the organization's project management activities.
— 8.9 - Configurations, including security configurations, of hardware, software, services and networks should be established, documented, implemented, monitored and reviewed.
Summary
Harness recognizes that achieving a robust and secure software delivery process demands a platform tailored to both the unique business needs of a company, and the stringent security and compliance standards those companies need to uphold. As we continue to build and expand on our modern software delivery platform, incorporating advanced enterprise security features to satisfy both Harness’ and our customer’s security and compliance requirements will remain an essential component of our platform.
Interested in learning more about how your organization can leverage the security features offered within the Harness Platform? Please request your demo today.
Have additional security or privacy questions or concerns? Email us at trust@harness.io.
