
Harness's Security Testing Orchestration is now generally available, providing automated security scans, intelligent vulnerability management, and customizable governance policies. It integrates seamlessly into CI/CD pipelines, enabling developers and security teams to collaborate effectively and enhance secure software delivery.
Since we announced the public preview for Harness STO module earlier in March this year, we’ve received valuable insights from end users about how they’re using Harness STO to increase velocity and security without compromising their current software delivery and application security. Based on their utilization of the module, we’ve incorporated this valuable end user feedback into several key new features, which we are now excited to announce with the General Availability (GA) of the Harness STO module.
These new STO features deliver business value to customers more quickly by increasing security throughout the entire software delivery process while reducing vulnerabilities and increasing innovation velocity.
Let’s walk through these new features and the capabilities they provide to engineering organizations.
Orchestrate Scanners Inside Harness CD and Standalone Pipeline
Harness STO integrates with multiple open source and commercial security scanners for secure pipeline development and security testing. Orchestrating application security scanners across software delivery and processing the output of the scanners allows for both enhanced application security and high delivery velocity. STO can be configured to be used with Harness CI/CD or in a standalone mode, integrating with any CI/CD tooling.

Security Exemption Review Between Developers and Security
Security vulnerabilities identified during security testing, while often important, are not always actionable, or in some scenarios, they may not be applicable to specific development environments or product scope. In some instances, there might be additional complexity in resolving a security issue immediately, but it may be more feasible to remediate with additional planning. For these reasons, security exemptions are an important parcel of secure software development lifecycle. Security stakeholders can grant and manage exemptions on vulnerabilities or issues identified from security scans during various software development stages via Harness STO.

Comprehensive Dashboards and Reporting
The STO dashboards provide a centralized source for aggregating multiple security scanner outputs with customizable views based on roles within the organization. Tailored dashboard views cater to specific organizational needs, providing a common place for security practitioners and developers to collaborate from and to prioritize, remediate, and address code vulnerabilities.

Governance Policies Based on the Open Policy Agent (OPA)
Harness STO empowers teams to customize governance configuration and enforce requirements as part of the CI/CD pipeline with customizable policies based on the Open Policy Agent (OPA) standard. This provides flexibility to define governance policies as needed across the organization and ensure that code being deployed meets the organization's specific security standards.

Integration: Role Based Access Control, Audit Trails, and Enterprise Platform Features
Audit trails are a valuable resource for security admins and auditors who want to examine suspicious activity or to diagnose and troubleshoot issues. Harness provides detailed, enterprise-grade audit trails for technical teams to quickly review and grade audits in a matter of minutes versus days. Harness’ granular role-based access control (RBAC) restricts system access to authorized users, allowing admins to implement permissions that meet the unique requirements of the business. While Harness STO works great as a standalone module, it’s even more powerful when paired with Harness CI/CD, allowing for native integration into pipelines.


Security Throughout The Entire Software Delivery Process
Harness STO brings DevSecOps principles to CI/CD pipelines and provides a fresh approach to ensuring that increased software velocity is achieved with a high degree of security. In order to empower development and security teams, a combination of automation and intelligent processing is paramount.
Development teams can now quickly analyze the output of application security scanners early in order to remediate security vulnerabilities, supporting the effort to increase release velocity while ensuring secure delivery of their software applications. While not to be equated with a security scanner, Harness STO is an orchestration solution that integrates with leading application security scanners. When CI/CD pipelines are executed, the data from all these scanners is normalized, deduplicated, and correlated, resulting in a prioritized list of vulnerabilities that engineering teams can take immediate action to resolve.
In addition, Harness STO customizes governance configuration and establishes consistent processes that ensure policies and procedures have been met. This enables compliance teams to better understand the type of security vulnerabilities and associated risks, helping them enforce compliance standards and policies. With Harness STO, enterprises can decrease their security risk while reducing time-consuming rework, resulting in greater productivity, overall business efficiency, and business value.
Primary Use Cases
Harness STO is a valuable tool for software developers, DevOps teams, DevSecOps engineers, and application security testing teams that are looking to deliver highly secure code while accelerating deployment velocity and minimizing rework. STO can be used in a variety of ways with a range of powerful capabilities. These include:
Security Testing Throughout the Software Delivery Process
Harness STO ensures that application security issues are identified, prioritized, and remediated immediately. By shifting left, security vulnerabilities can be caught much earlier in the development cycle, so testing orchestration can occur throughout the software delivery process by the various stakeholders.
Developer-First Remediation
STO’s intelligent scanner analysis engine helps developers categorize new and existing vulnerabilities, analyze and deduplicate across multiple security scanners, and prioritize remediation. This saves organizations countless hours and money by finding and fixing these issues early on.
Governance, Dashboards, and Reports
Harness STO has a centralized console that is customizable for developer, security, and executive management teams. Enterprise dashboards and reports provide a role-based view of application security risk.
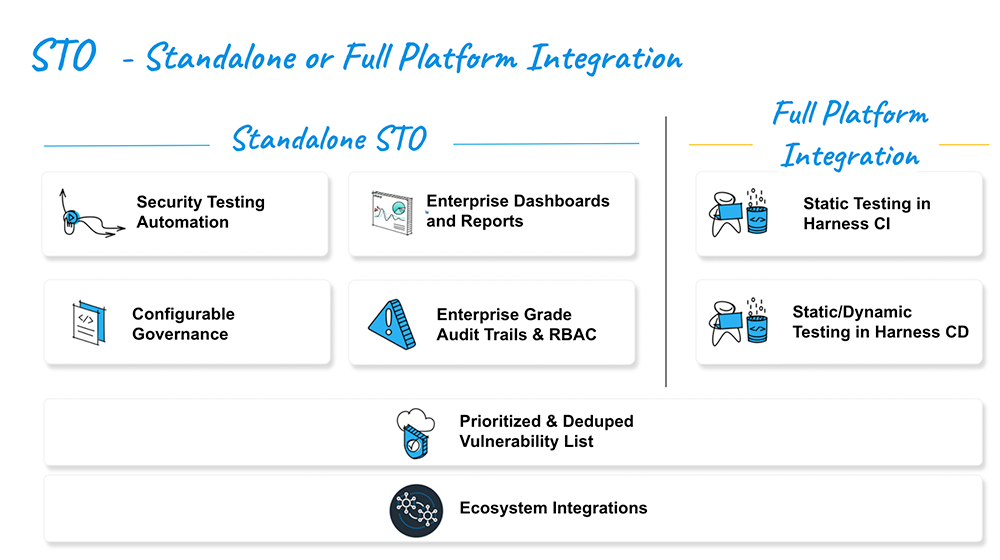
Key Capabilities
Harness STO works seamlessly with the Harness CI and CD modules and as a unified platform, a combination that delivers a holistic solution with tremendous value. Harness STO is available as a standalone module with support for SaaS, on-prem, or hybrid deployment models.
Security Testing Automation
With the capability to create and execute application security testing pipelines, organizations can invoke Harness STO from within their CI/CD pipelines and benefit from the centralized and analyzed scanner results.
Configurable Governance
Harness STO has built-in governance based on the Open Policy Agent (OPA), which provides the flexibility to define policies as needed across an organization. It also allows groups to define what scanners need to be run at what stages, along with what constitutes acceptance or failure from these scanners, and to make changes to policies as required.
Enterprise Dashboards and Reports
Customized views can be created for different roles within the organization. Harness STO allows administrators and security owners to generate application security reports that can consolidate data across user groups and tools.
Enterprise Grade Audit Trails and RBAC
Harness STO provides detailed audit trails to help companies meet compliance or IT policy requirements. It also facilitates better security governance by providing actionable audit information. This transforms what normally would take days of effort to produce into just a few hours. The RBAC model allows implementation via a role based permissions system to satisfy unique organizational requirements.
Static Testing in Harness CI
Static Application Security Testing (SAST) and Software Composition Analysis (SCA) are used to analyze an application’s code, typically during the build and test phases. Harness STO makes it easy to integrate SAST and SCA into existing CI pipelines.
Static or Dynamic Testing in Harness CD
For deployment, similar to CI, you can use a CD stage to call a Harness security testing pipeline and obtain the centralized analysis engine data.
Prioritized and Deduped Vulnerability List
Harness STO’s intelligent scanner analysis engine significantly reduces the workload of the engineering team. It collects the disparate output from all supported security scanners, normalizes, deduplicates, correlates, and produces a prioritized list of vulnerabilities to remediate.
Ecosystem Integrations
STO integrates with the most popular application security scanners.
Learn More About The Harness STO Module
If you’re interested in seeing Harness STO in action, schedule a personalized demo today!
