
Boost Your DevSecOps Practice With SLSA-based Artifact Integrity and SBOM-driven Open Source Governance
If you’ve instituted a shift-left security approach where application developers are handily remediating code vulnerabilities without last-minute toil, your DevSecOps practice is off to a great start. But like the vast majority of organizations building modern applications, your company’s software probably comprises a variety of open-source artifacts and other third-party components whose integrity the company is on the hook to ensure. Why? Look no further than the Solarwinds, Log4j, and Codecov breaches to see that a single, compromised artifact can wreak havoc for tens or hundreds of thousands of the software’s consumers. For the purpose of preventing these types of destructive cyberattacks, a ubiquitous framework for hardening the software supply chain is required.
Executive Order 14028 was issued for the purpose of strengthening the United States’ cybersecurity posture and requires organizations to implement safe development practices and maintain greater visibility into their software and its artifacts. EO 14028 has accelerated the adoption and standardization of Software Bills of Material (SBOMs) as a means of accounting for and ensuring the integrity of an application and all of its artifacts. The SBOM provides a critical layer of transparency and security, and its lifecycle management is a vital capability of a successful DevSecOps program. To comply with EO 14028, organizations need to adopt a framework like SLSA that aligns with NIST recommended SSDF to ensure artifact integrity, and generate SBOMs.
Introducing Harness Software Supply Chain Assurance (SSCA)
Building on the integrated, platform approach to DevSecOps that the majority of software-producing organizations are seeking, we're excited to introduce Harness SSCA today at Unscripted!
Harness SSCA extends application security beyond your own application code to the whole supply chain, enabling you to monitor and control open source software components and third-party artifacts, generate comprehensive SBOMs for enhanced visibility, and guarantee software integrity in accordance with SLSA and Executive Order 14028 requirements.
Here’s an overview of the SSCA module’s key capabilities:
Software Integrity based on SLSA
Supply-chain Levels for Software Artifacts (SLSA) is an important framework for creating a secure software supply chain. It lays out practices and guidelines to help you securely build your software and prove that it is not tampered with as it moves through different stages of your pipeline. Harness SSCA ensures the integrity of software by generating and validating the provenance (such as build source, branch, etc.) as per SLSA v1.0 specifications.
SBOM Orchestration and Lifecycle Management
The SSCA module offers users the flexibility to select their preferred tools for generating SBOMs in both CycloneDX and SPDX formats. Moreover, it empowers users to sign and validate SBOMs using their private keys, ensuring secure storage and sharing with software consumers.
Visibility and Control Of Open Source Software
With approximately 80% of a typical software application relying on open source software, the SSCA module offers deep visibility into the usage of open source components across all artifacts and their deployments. Further, it enables users to enforce policies by granting or restricting the use of components based on their versions, license, suppliers, and PURL.
A Look At Harness SSCA
Let’s take a brief tour of Harness SSCA. We’ll step through some of the workflows DevOps engineers and security analysts would undertake in generating SLSA provenance and SBOMs, verifying SLSA provenance, and enforcing policies to ensure that any risky open source software artifacts do not pass through to the deployment.
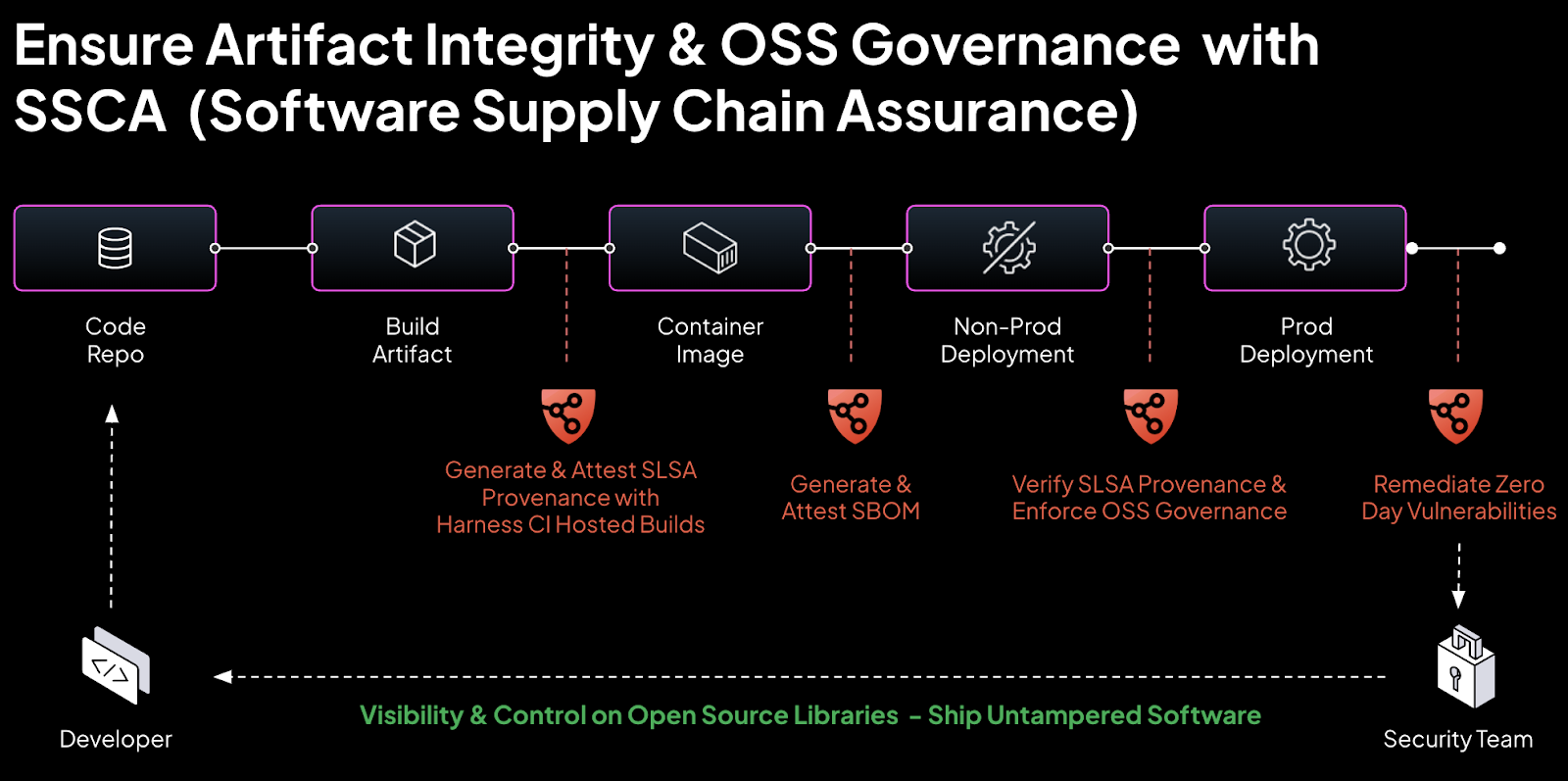
Guaranteeing that your application maintains its integrity throughout its journey through the pipeline begins with enabling SLSA.
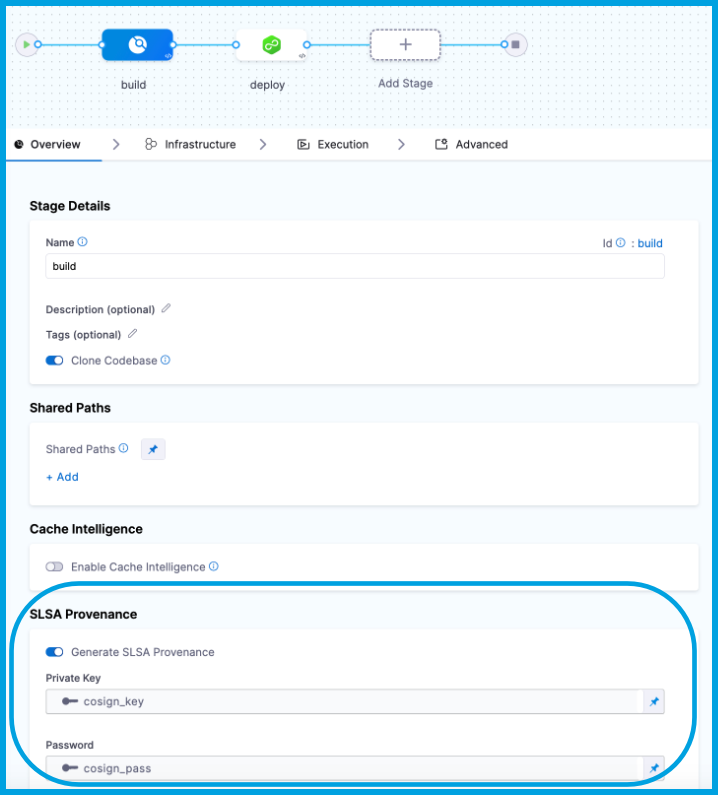
SLSA Generation And Attestation
With the Harness SSCA module, you can achieve SLSA Level 2 compliance by generating SLSA provenance according to the SLSA v1.0 specification. While SLSA level 1 stipulates that provenance exists, showing how a particular software package was built (what entity built the package, what build process they used, and what the top-level input to the build were), SLSA level 2 adds the requirement that the particular build runs on a hosted build platform that generates and signs the provenance itself.
In generating SLSA provenance within the build pipeline, you need to first generate a key pair using Cosign, as shown in the screenshot below.
SBOM Orchestration And Generation
A Software Bill of Materials (SBOM) is essential for understanding the components and dependencies within an application, which in turn enables your organization to manage open-source component risks effectively.
The Harness SSCA module generates, manages, and analyzes SBOMs for software artifacts. Below is the SSCA workflow for generating a SBOM:
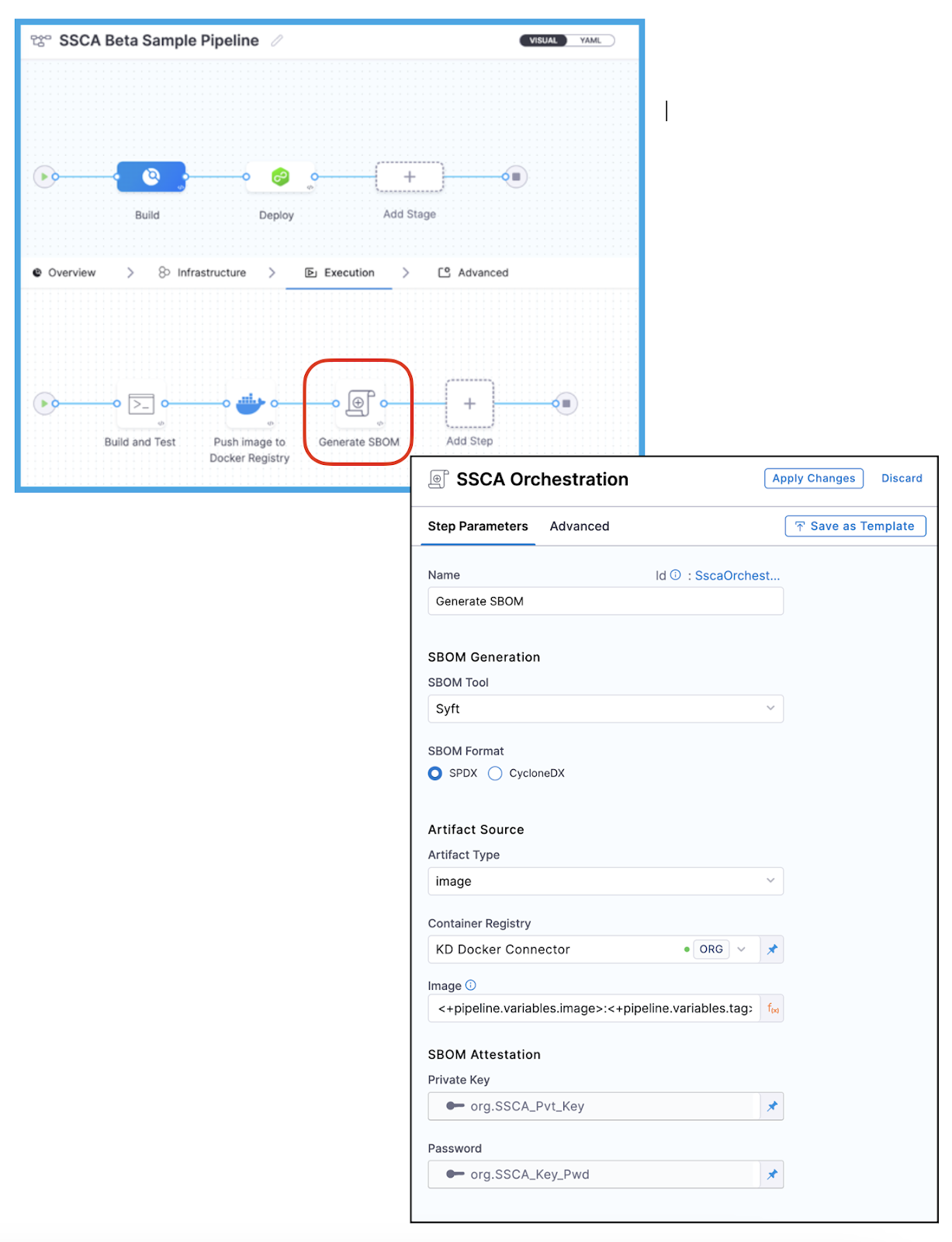
SSCA supports SPDX and CycloneDX formats for SBOM generation and tools such as Syft and Cosign. When an SBOM is generated, the SSCA module generates and signs the attestation, ensuring that the information is accurate and trustworthy. The attestations are then securely stored in your artifact repository, where you can access and analyze them as needed.
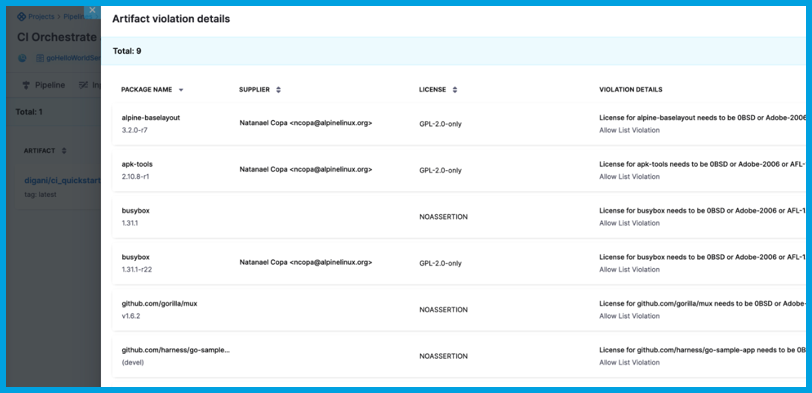
OSS Governance Through Policy
With Harness, you have full control over their use throughout CI and CD stages via the SSCA module’s policy management and enforcement capabilities. As you seek to deploy only compliant artifacts, you can put two types of policies into effect:
- Deny list policies: Define components, or combinations of component attributes, that are not allowed. If an artifact includes a component that is part of the deny list, the artifact's policy evaluation fails.
- Allow list policies: Define components or combinations of component attributes that are allowed. If an artifact includes a component that is not part of the allow list, the artifact's policy evaluation fails.
When an artifact moves through your pipelines, the SSCA module checks the artifact and its associated SBOM against your defined policies. Policy violations are tabulated and displayed in detail.
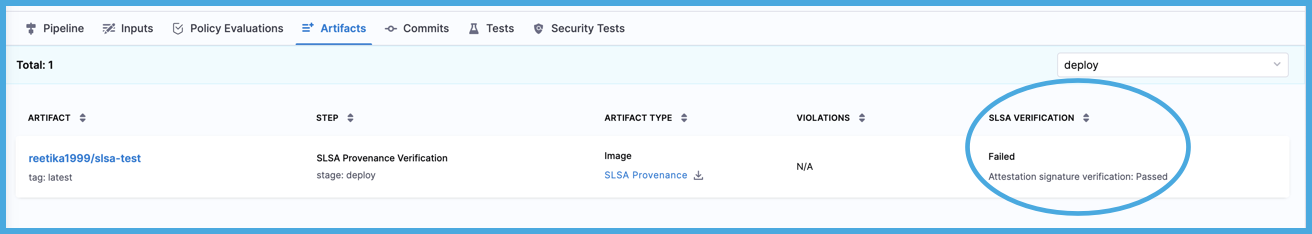
SLSA Verification
You can use Harness SSCA to verify SLSA provenance using an OPA policy. In the example below, we are ensuring integrity of the application by validating the branch name on which it was built in the deploy
Software Supply Chain Assurance, the Harness Way
More and more enterprise organizations are taking a platform approach to building out their DevSecOps practices, and a big reason why customers come to Harness is the seamless integration of critical security capabilities such as Security Testing Orchestration (STO). Harness SSCA follows suit, delivering powerful OSS governance and SLSA compliance features.
To learn more about Harness SSCA, visit Harness Software Supply Chain Assurance
Interested in seeing Harness SSCA in action? Sign up for a demo!
