
OpenID Connect (OIDC) enhances security and user experience by simplifying authentication and managing permissions, enabling secure software deployments with Harness. It eliminates password storage, uses short-term tokens for reduced risk, and supports regulatory compliance, streamlining user management and access control.
As authentication complexities grow, have you ever wondered how effortlessly you can switch between different applications without remembering multiple passwords? All you need to do is click an option like "Sign in with <any social account>," and with just one click, You are authorized, and the application is now ready for use.
Sounds simple, right? But behind the scenes, you're actually using a powerful authentication method that not only verifies your identity but also determines what actions you're allowed to perform within the application.
In this article, we will explore and focus on a authentication method specifically —OpenID Connect (OIDC). We will discuss what it is, how it works, how companies leverage it for security and user experience, and how Harness uses OIDC to ensure secure software deployments.
What is OpenID Connect (OIDC)?
OIDC is an authentication protocol built on top of OAuth 2.0. It provides a standardized way to verify user identities for an application while ensuring both security and convenience.
It acts as a digital identity card for the internet, enabling secure access to different applications without the need to manage multiple passwords. It simplifies the authentication process by adding an identity layer to OAuth 2.0.
OIDC ensures that only legitimate users can log into an application, while OAuth 2.0 determines what actions and permissions the user is allowed to perform. One of the benefit of OIDC is short-term token which reduces the blast radius.
Key Components of OIDC
To understand the functionality, let’s begin by dissecting the five essential components and examining how they interact cohesively.
- Relying Party: This can be any application that needs to verify user identities. For example, when you use "Login with Google" on a website, the website acts as the Relying Party—it relies on Google to verify your identity.
- Identity Provider(IdP): An Identity Provider (IdP) can be thought of as a trusted authority, like Google, Microsoft, or Okta. They manage your account and verify your identity. When you log in using an IdP, it confirms who you are to other applications.
- ID Token: It is securely packaged information about you, also known as a JWT (JSON Web Token). It contains verified claims about your identity, such as your name, email, and login details.
- UserInfo Endpoint: Some applications require additional information about you that may not be available in the ID Token. This endpoint provides a secure way to fetch the missing information.
- Scopes and Claims: Scopes can be considered as consent requests that inform you about what information an application can access. Claims are the actual pieces of information shared when you approve a scope.
Working and User Journey with OIDC
OIDC offers users a seamless experience while guaranteeing secure access to various applications. The following key stages define the typical user journey with OIDC:
- Initiation: The user attempts to access a resource that requires authentication. This action prompts the application to redirect the user to the OIDC provider.
- Authentication: The user is presented with a login page by the OIDC provider. Here, they can enter their credentials or choose to authenticate using a social login option.
- Authorization: Once authenticated, the user is asked to grant permissions to the application requesting access to their profile information. This step ensures the user is aware of the data being shared.
- Token Issuance: Upon granting permission, the OIDC provider issues an ID token and, if applicable, an access token. These tokens are crucial for the application to verify the user's identity and access their information.
- Access Granted: The application receives the tokens and uses them to authenticate the user, allowing access to the requested resources.
- Session Management: The application manages the user session, which includes handling token expiration and renewal processes to maintain a secure and uninterrupted user experience.
Using the similar workflow, Developers can create more intuitive and secure applications that enhance user satisfaction while maintaining robust security measures.

Traditional Authentication vs OIDC vs OAuth 2.0
Implementing OIDC with Harness
Harness provides multiple options for using OpenID Connect (OIDC); however, in this section, we will focus on executing a pipeline with OIDC. We also encourage you to explore Single Sign-On (SSO) with OIDC, as we plan to share configuration details in future blog posts.
Secure your pipelines by configuring OIDC to ensure deployments run in a specific authorized environment. This section will guide you through configuring OIDC in GCP, requiring setup in both Harness and the cloud platform for secure pipeline execution.
Pre-requisites:
To begin the configuration process, we will need the following.
- Harness AccountId : Login to your harness account → Account Settings → Account Details. Save it for further configuration.
- To establish a connection to GCP using OIDC, you must first configure an OIDC Identity provider and link the service account with the necessary permissions that Harness will utilize for operations within GCP. This setup will enable you to configure the following:
- GCP workload identity provider, once completed you will be able to get
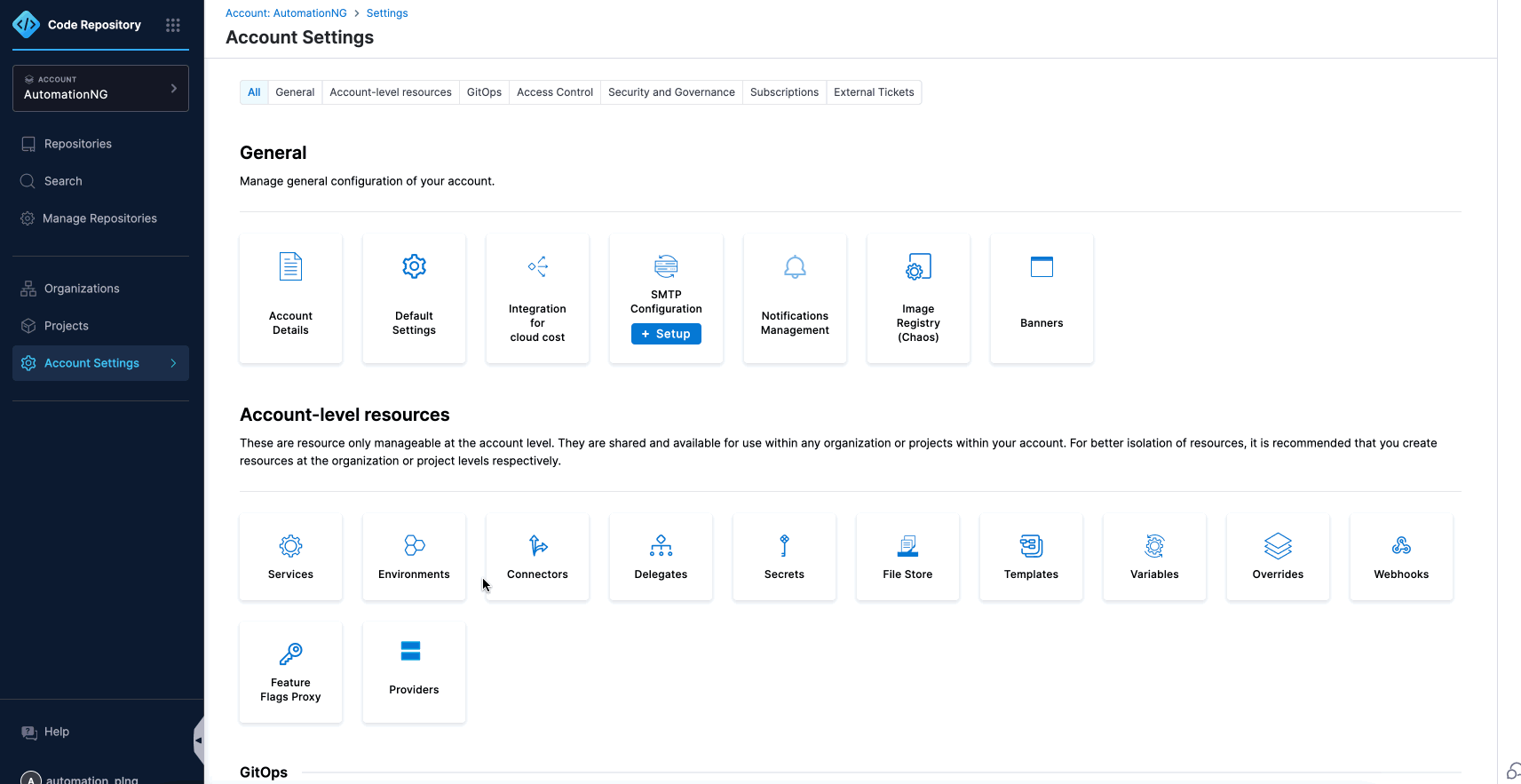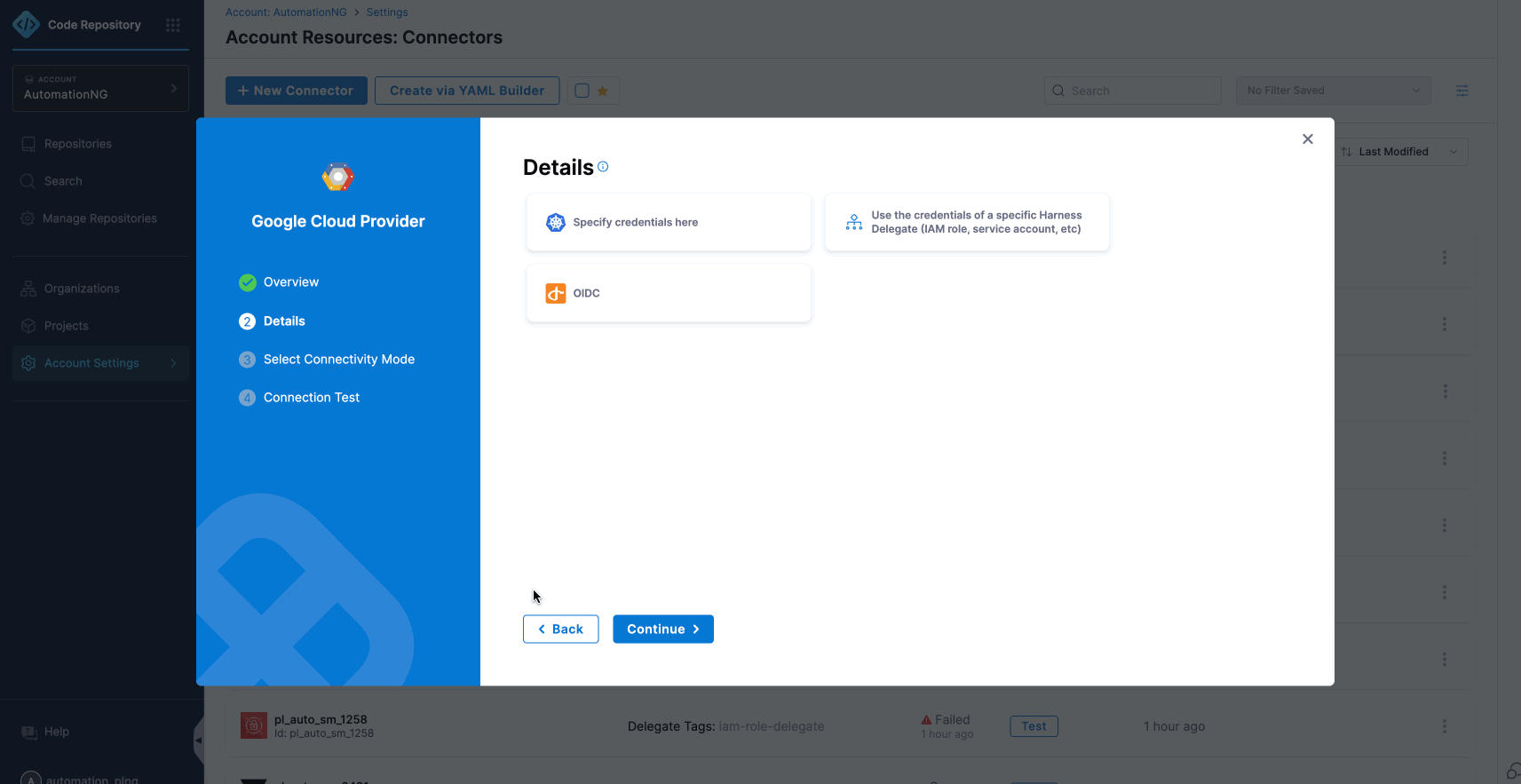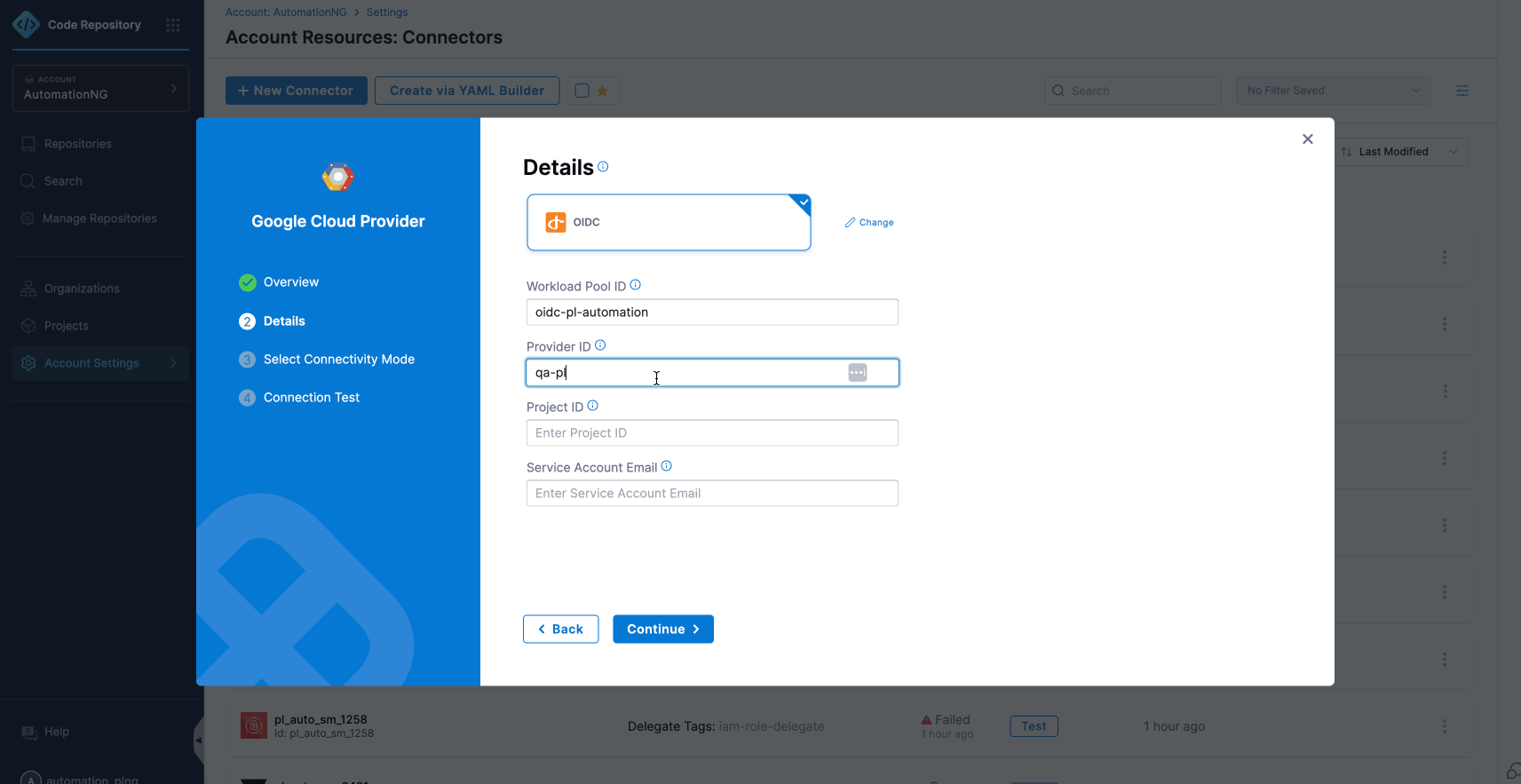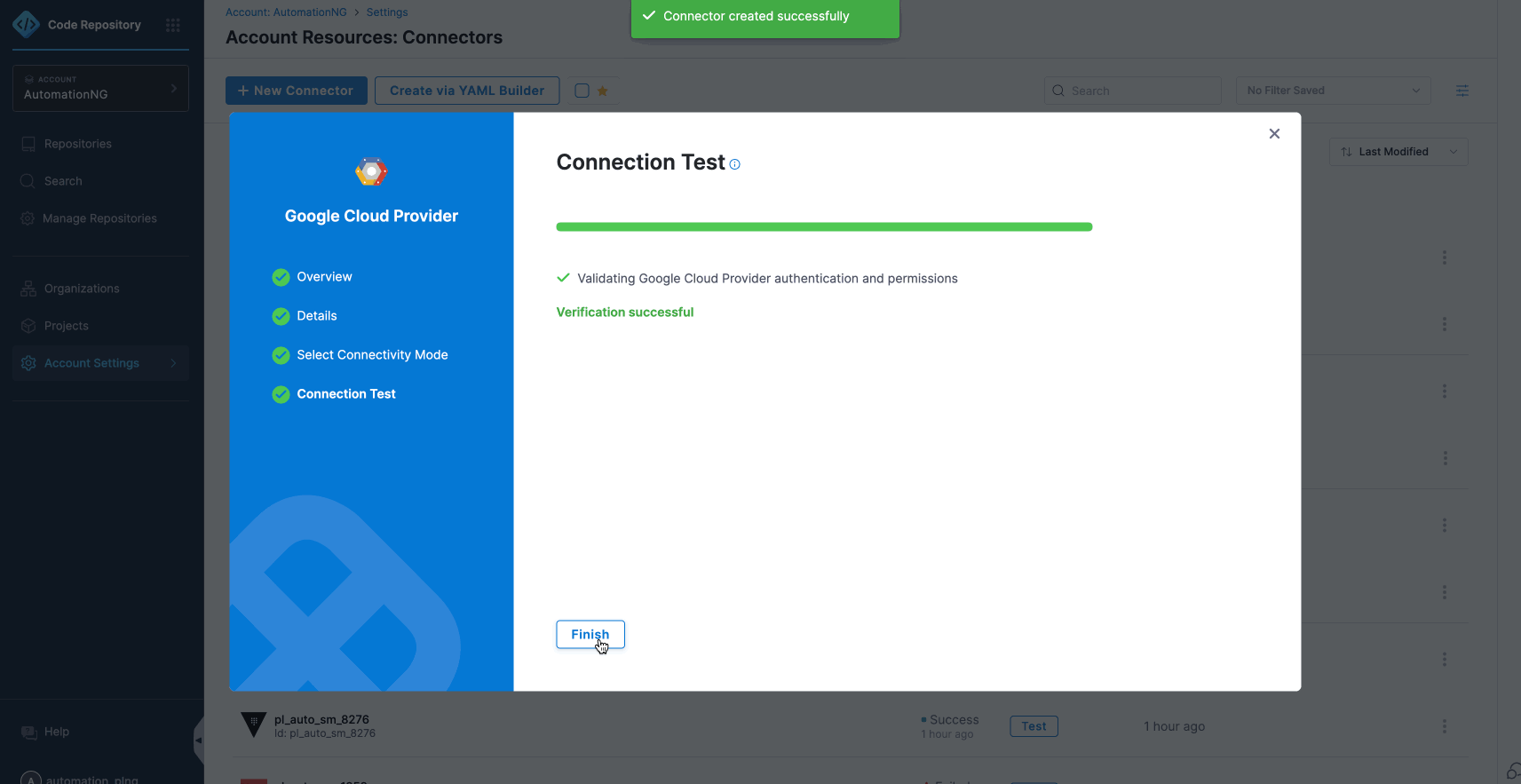
- Workload Pool ID
- Provider ID
- Project ID
- Service Account Email
- After completing the previous step, you will need the following to set up the GCP connector.
- GCP workload identity provider, once completed you will be able to get
- To set up your OIDC identity provider, please note below URLs to configure Harness OIDC provider endpoint and OIDC audience settings:
- For the Harness OIDC provider endpoint that will be used within GCP, replace
<YOUR_ACCOUNT_ID>with the Harness account ID you obtained in step 1.
- https://app.harness.io/ng/api/oidc/account/<YOUR_ACCOUNT_ID>
- Specify the OIDC audience
- https://iam.googleapis.com/projects/<YOUR_GCP_PROJECT_ID>/ locations/global/workloadIdentityPools/<YOUR_WORKLOAD_POOL_ID>/providers/<YOUR_PROVIDER_ID>
- For the Harness OIDC provider endpoint that will be used within GCP, replace
For information about these values, we recommend to got through the GCP documentation on Managing workload identity pools, Managing workload identity pool providers, and Creating and managing projects.
Configuring OIDC with pipeline
- To configure and verify the GCP connector, follow these steps:
- Navigate to Account Settings.
- Select Account-level resources.
- Click on Connectors.
- Choose Cloud Provider (GCP).
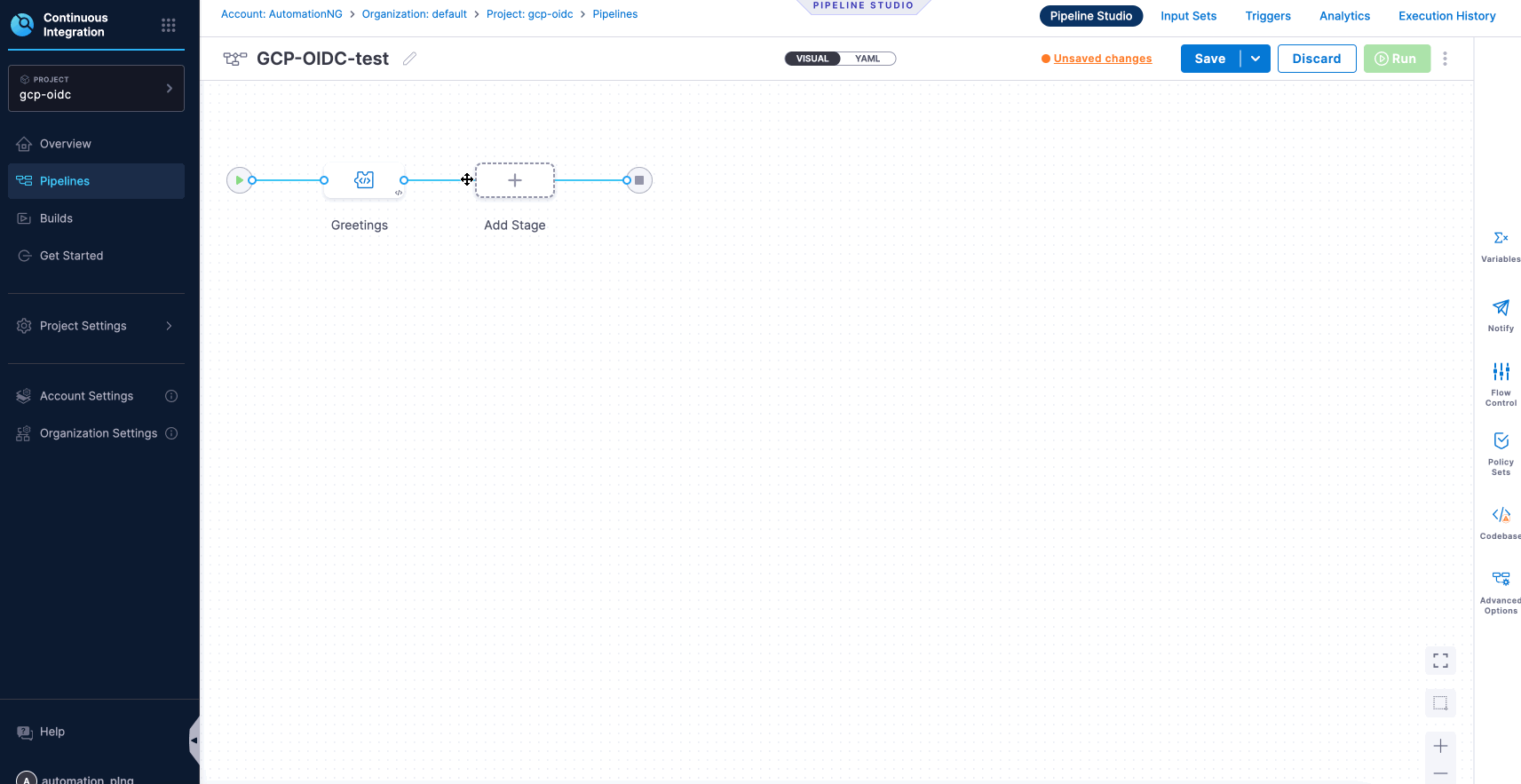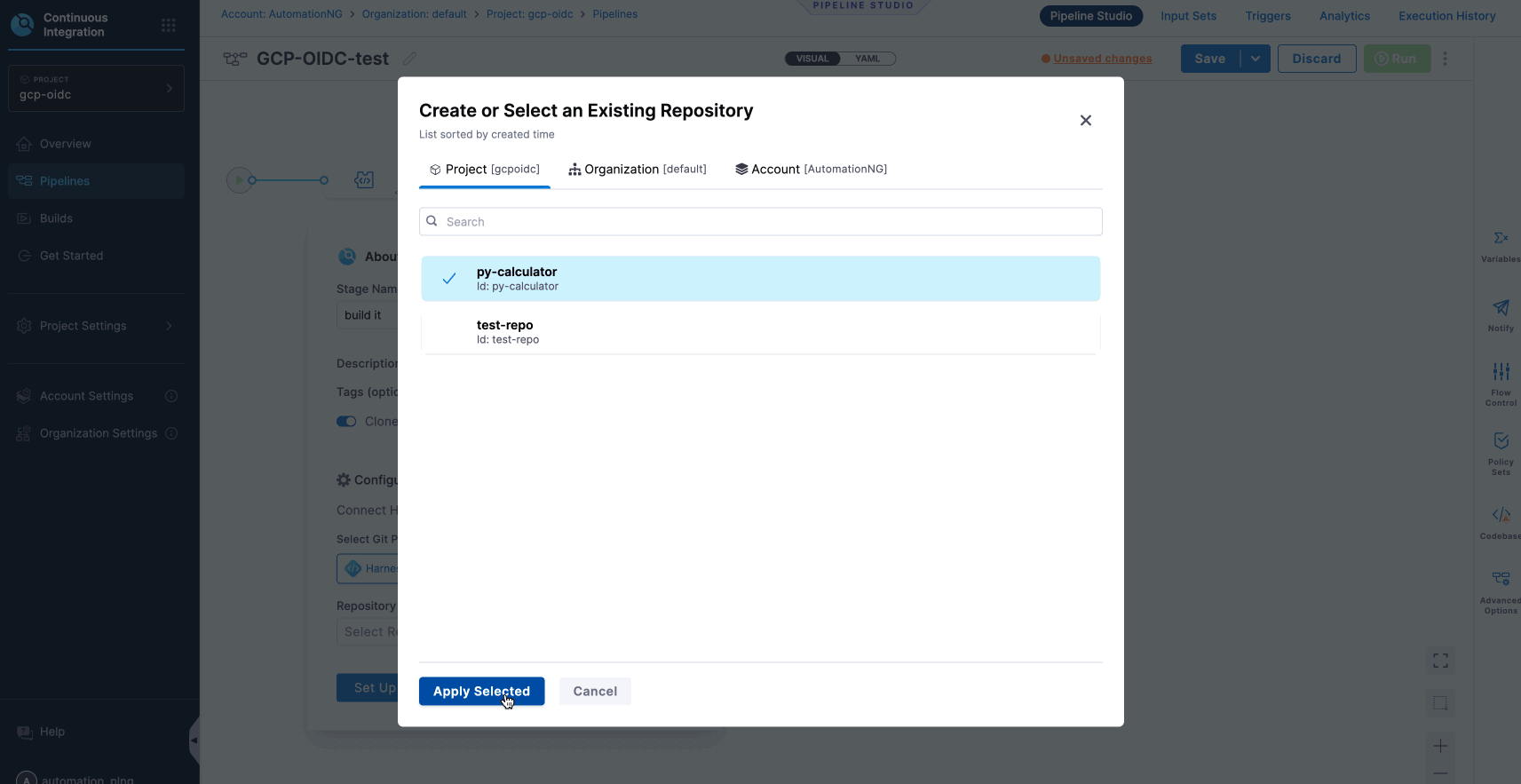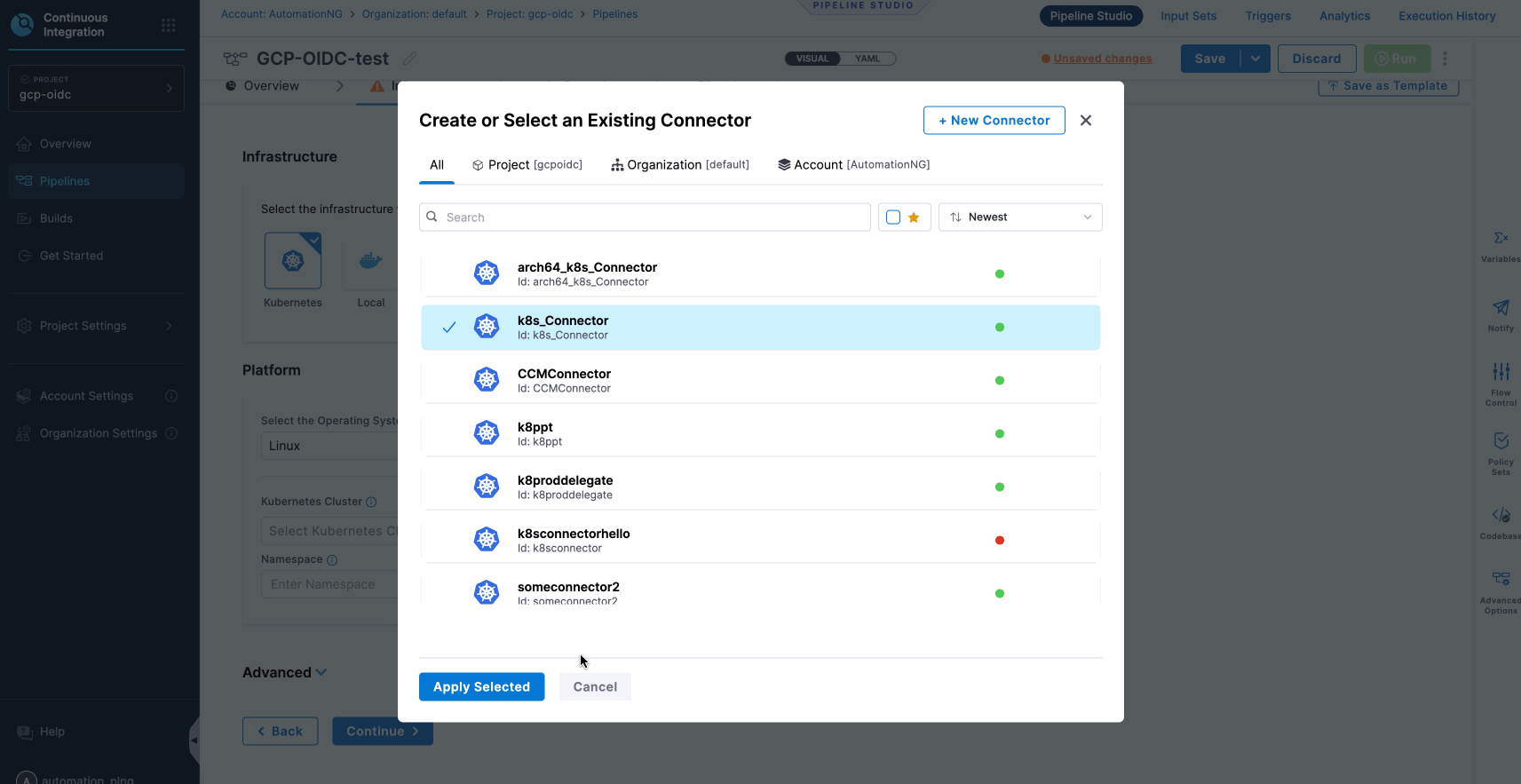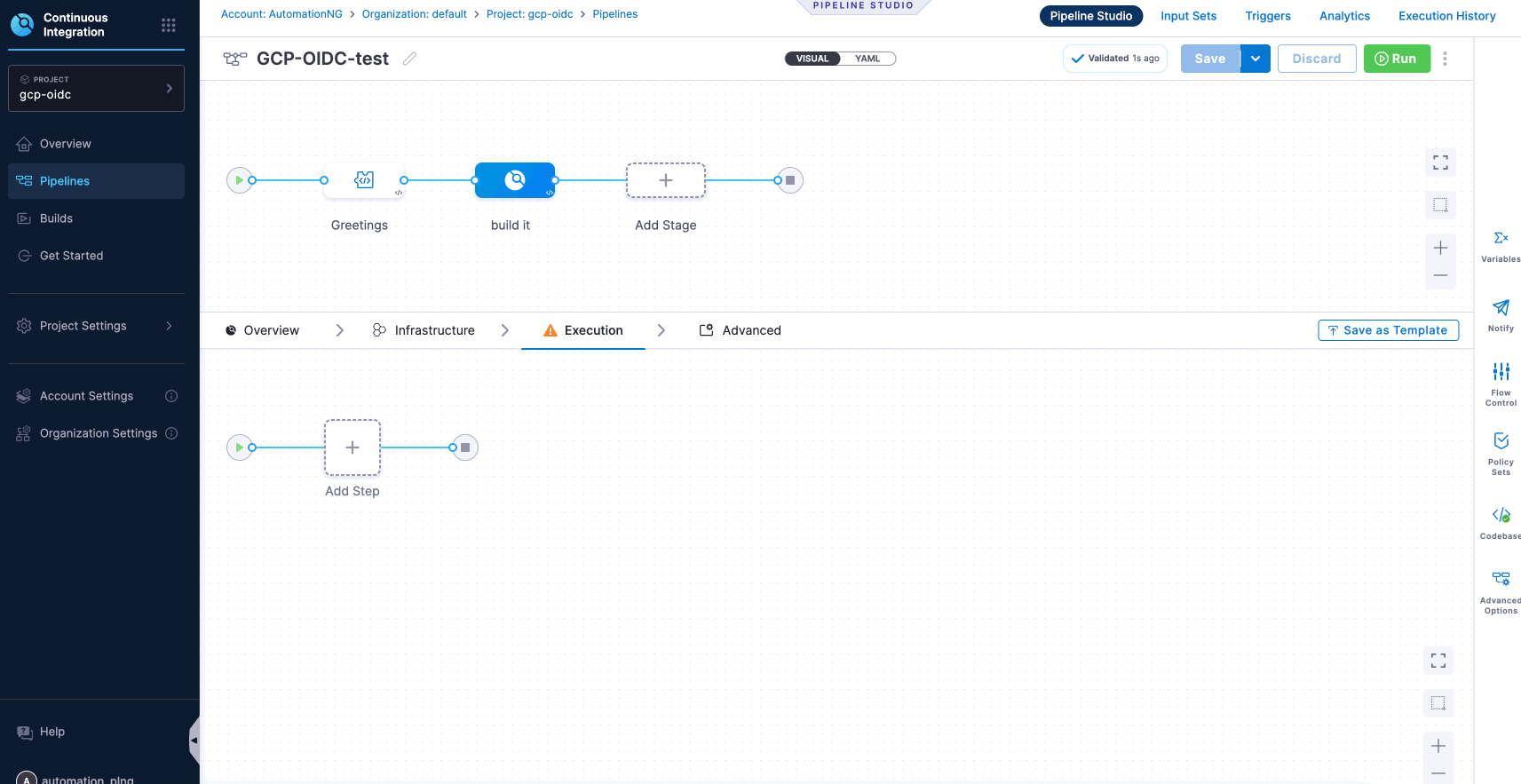
- Create and configure a codebase:
- To add or create your codebase in a Harness Code Repository, you will need to connect this repository or any third-party code repositories during the pipeline configuration process.
- We have already integrated a codebase into the repository, which we will connect within the pipeline.
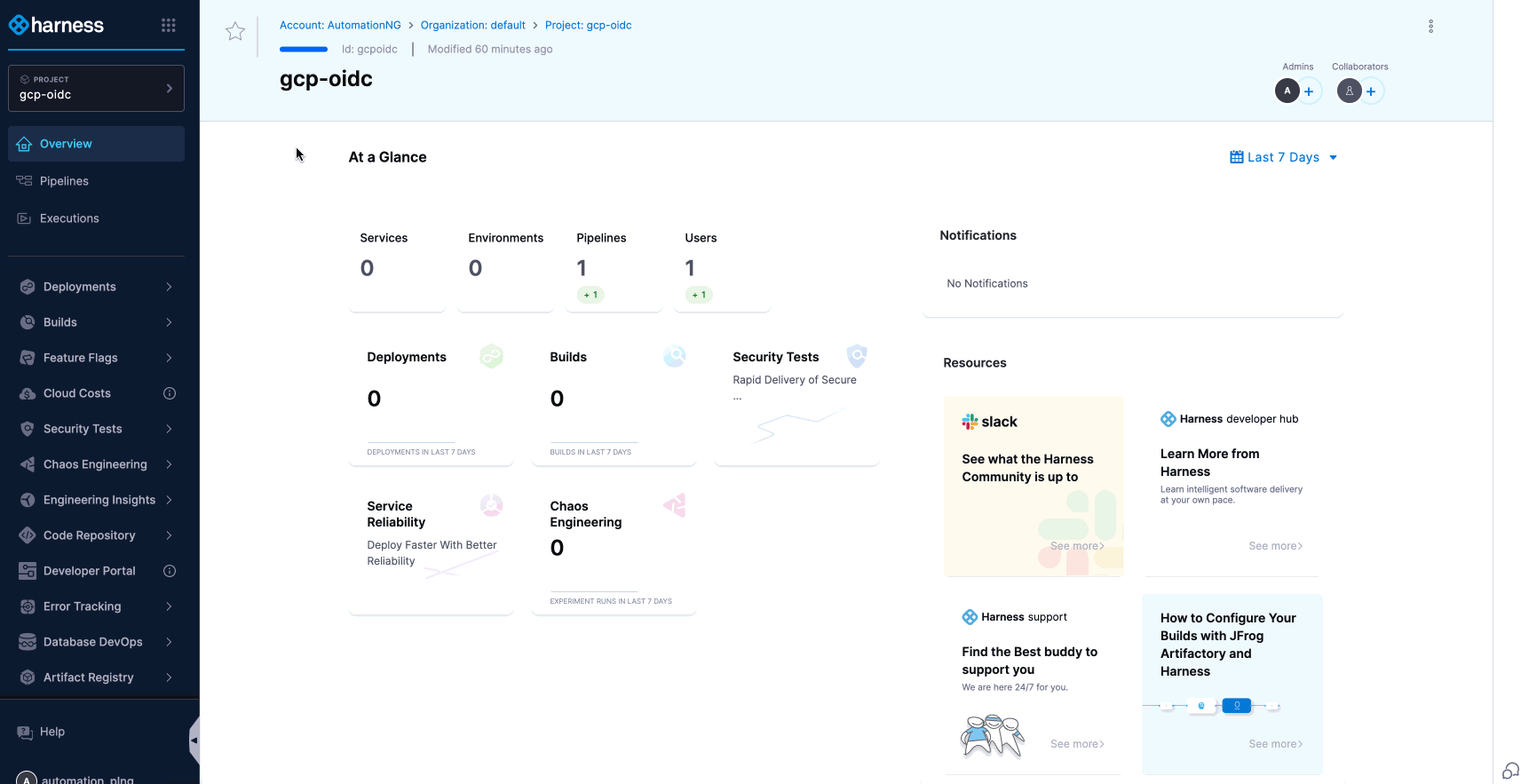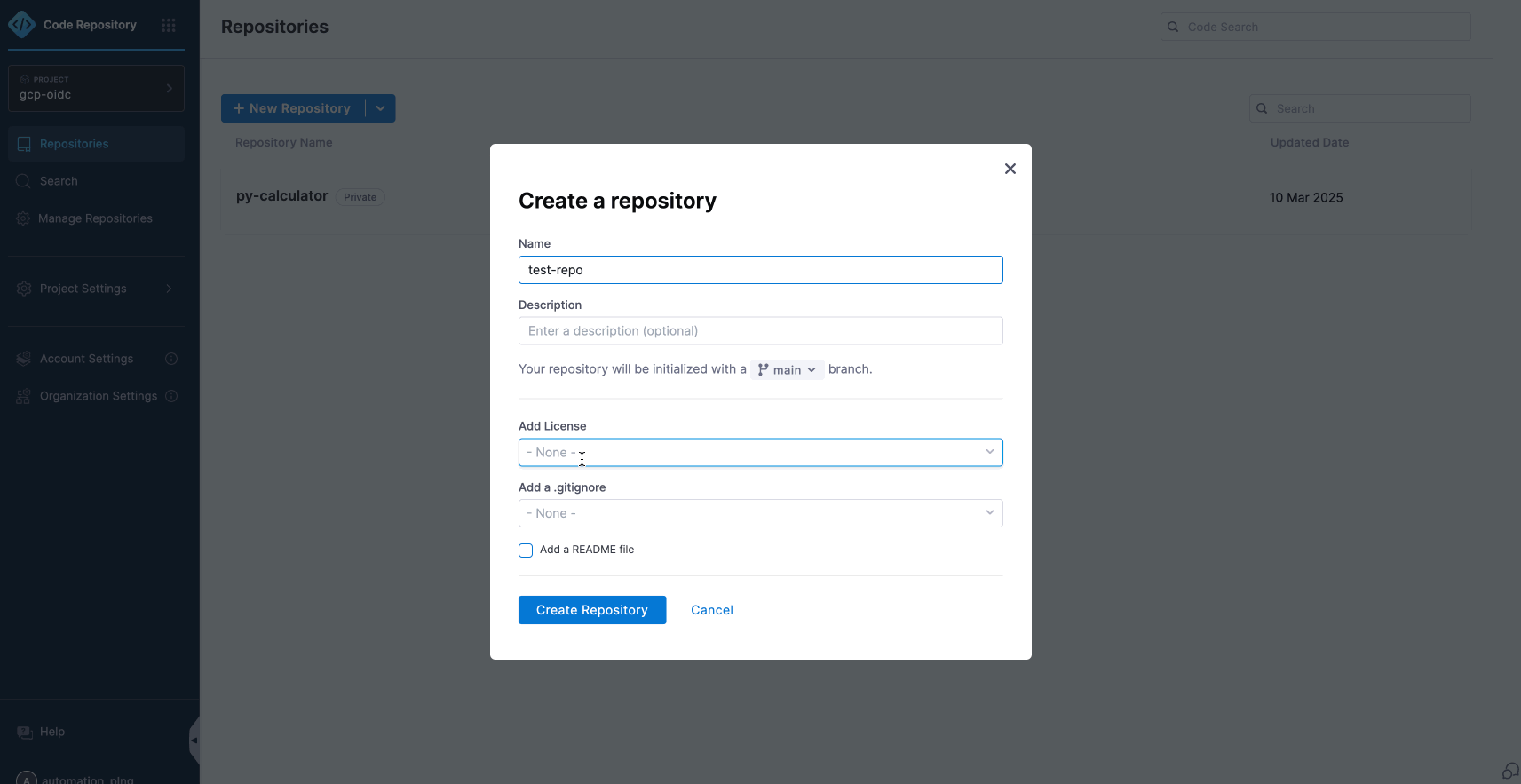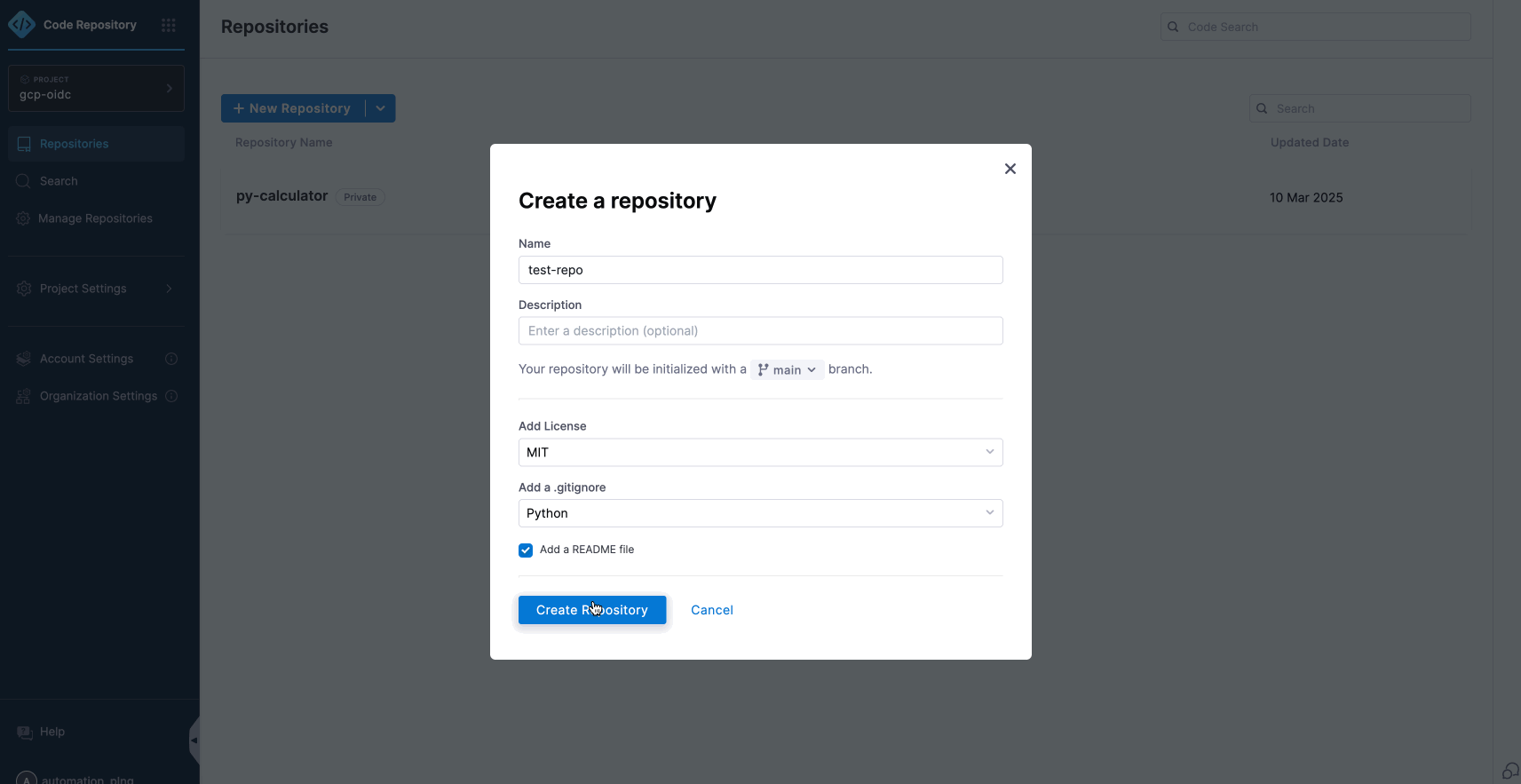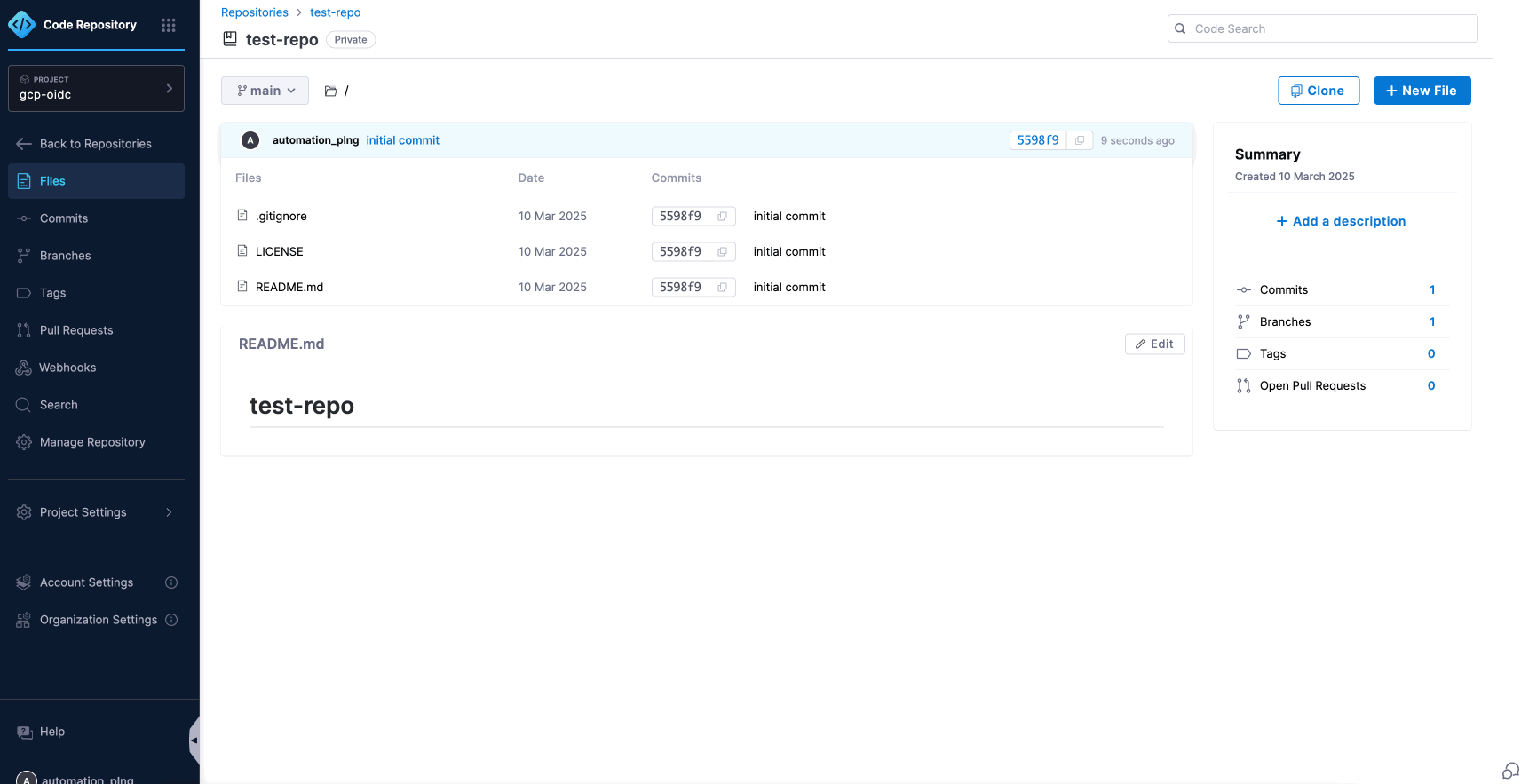
- To set up a Harness CI Pipeline.
- Navigate to Continuous Integration, then select Pipelines, and click on Create Pipelines.
- After finishing the initial steps, move on to the Build stage and set up the deployment of the codebase as illustrated below. For a comprehensive guide, you can refer to the detailed description here.
- The build stage consists of four steps: Overview, Infrastructure, Execution, and Advanced. For now, we will concentrate on the Infrastructure and Execution steps. These steps enable the configuration of pipelines using OIDC.
- To deploy your pipeline, begin by selecting one of the options within the Infrastructure stage, which includes Kubernetes, Local, and VMs. Choose the option that best meets your requirements, and then select the appropriate platform accordingly.
- Deploying a Pipeline with OIDC Environment:
To successfully execute the deployment of your application, it is essential to establish a clear sequence of steps. When deploying on Google Cloud Platform (GCP), ensure that you have your Host ID and Project ID prepared for configuration, as illustrated in the instructions below.
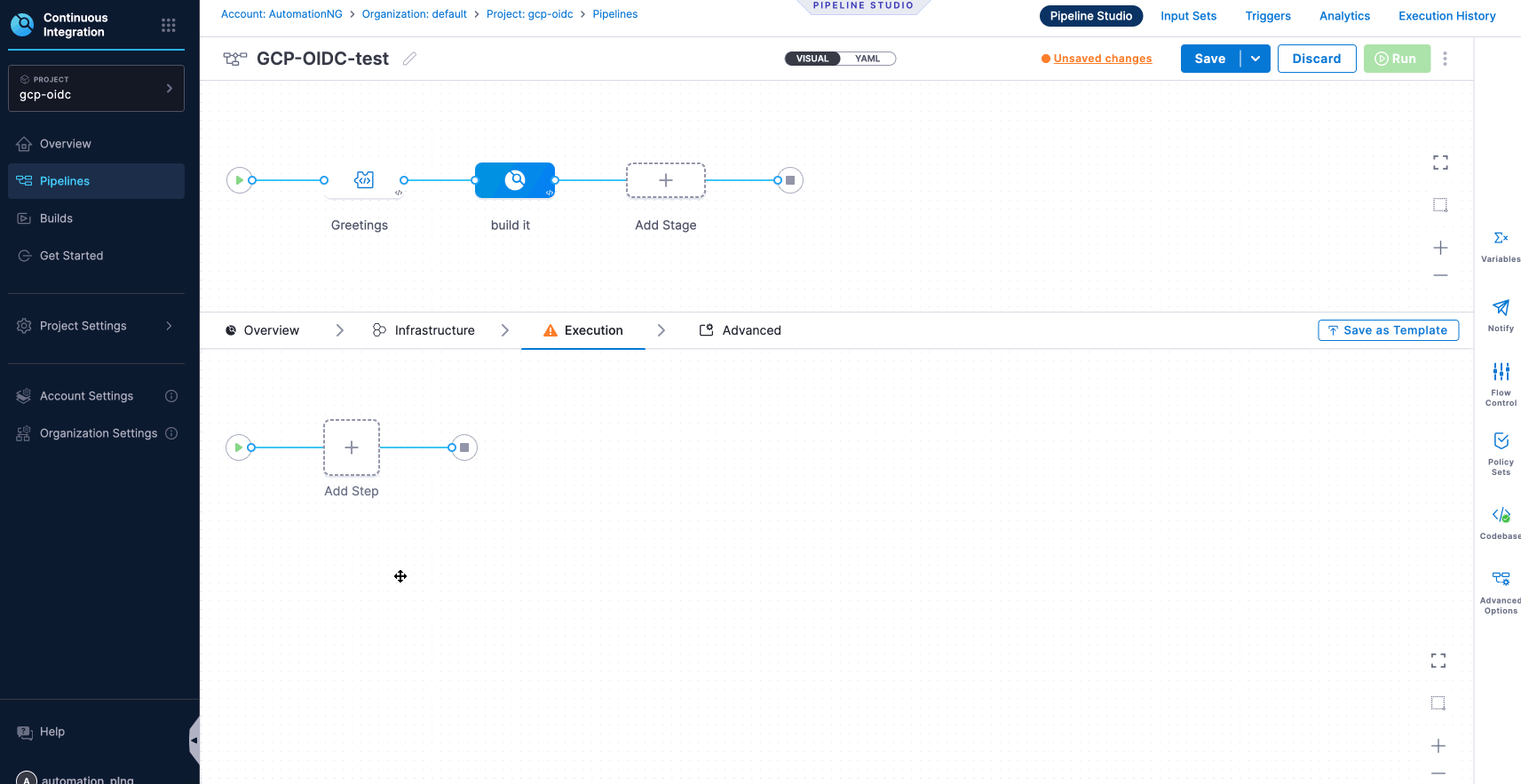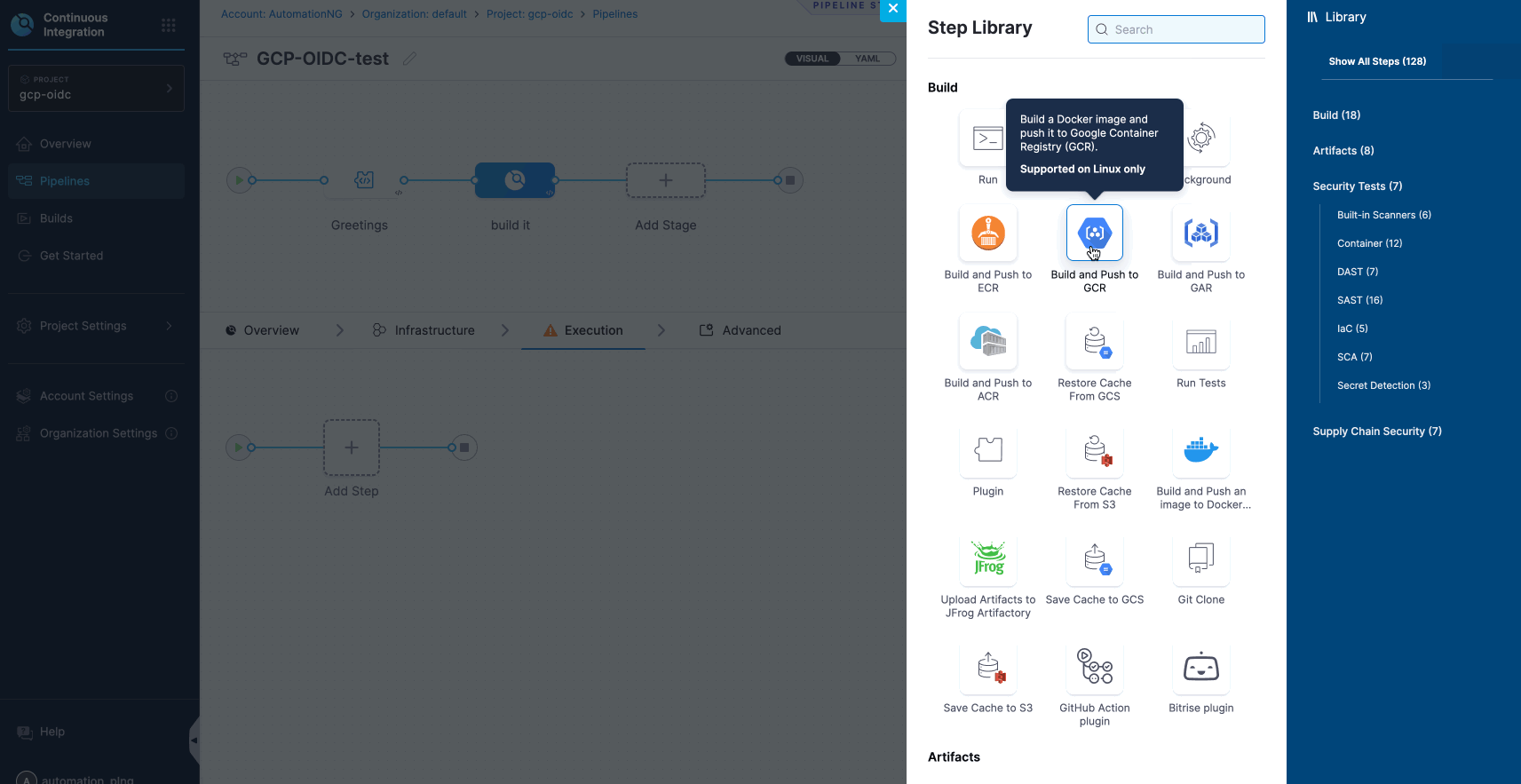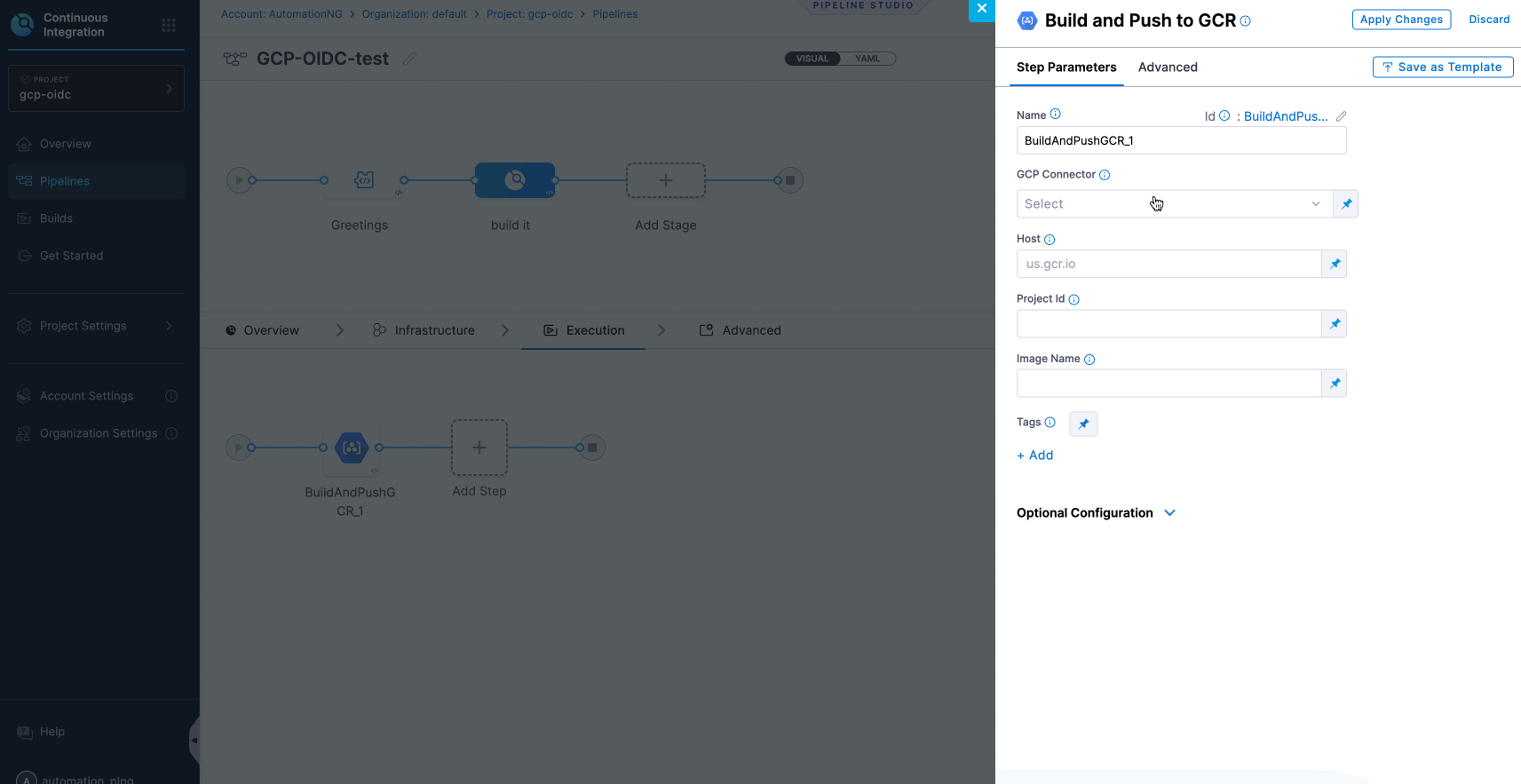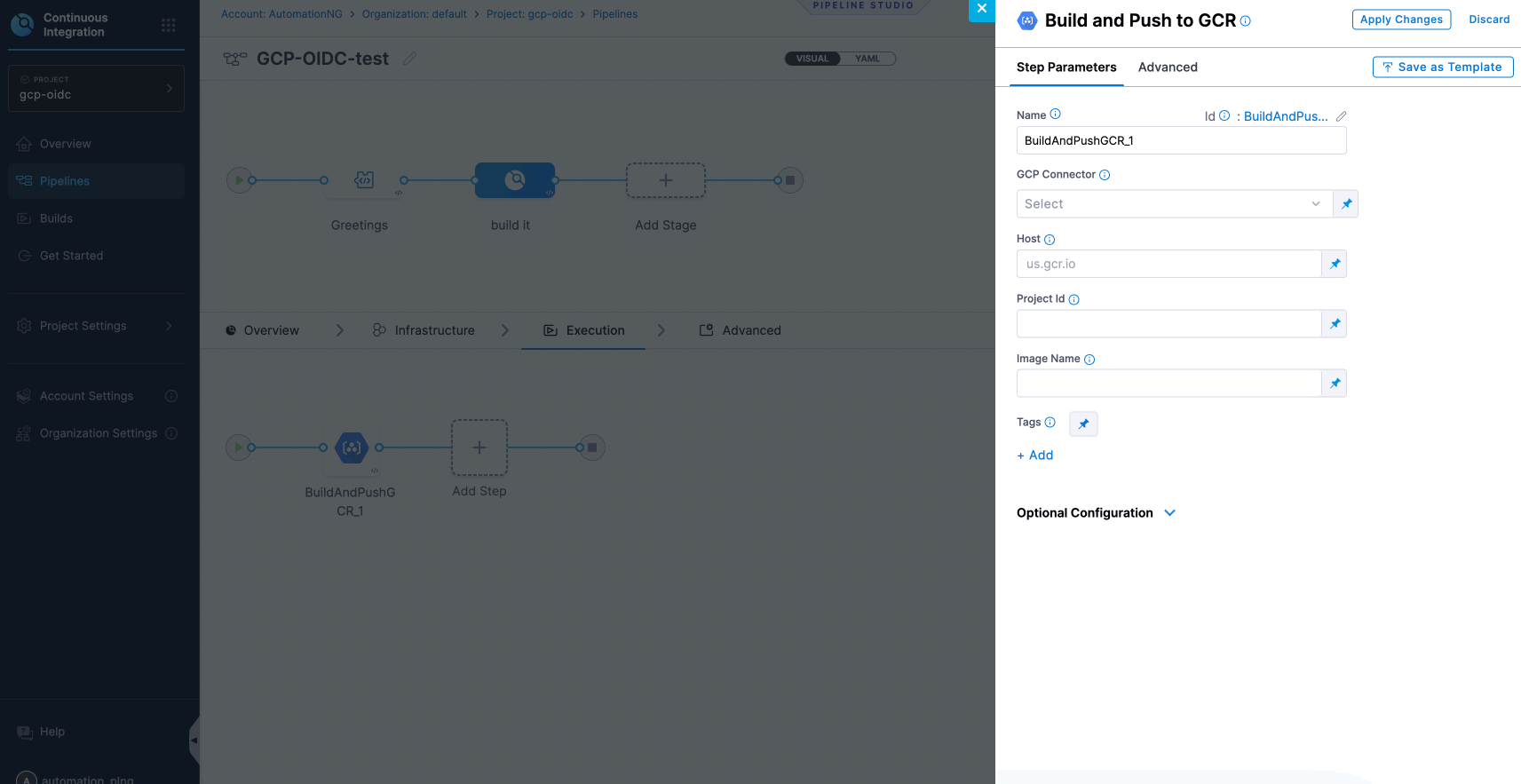
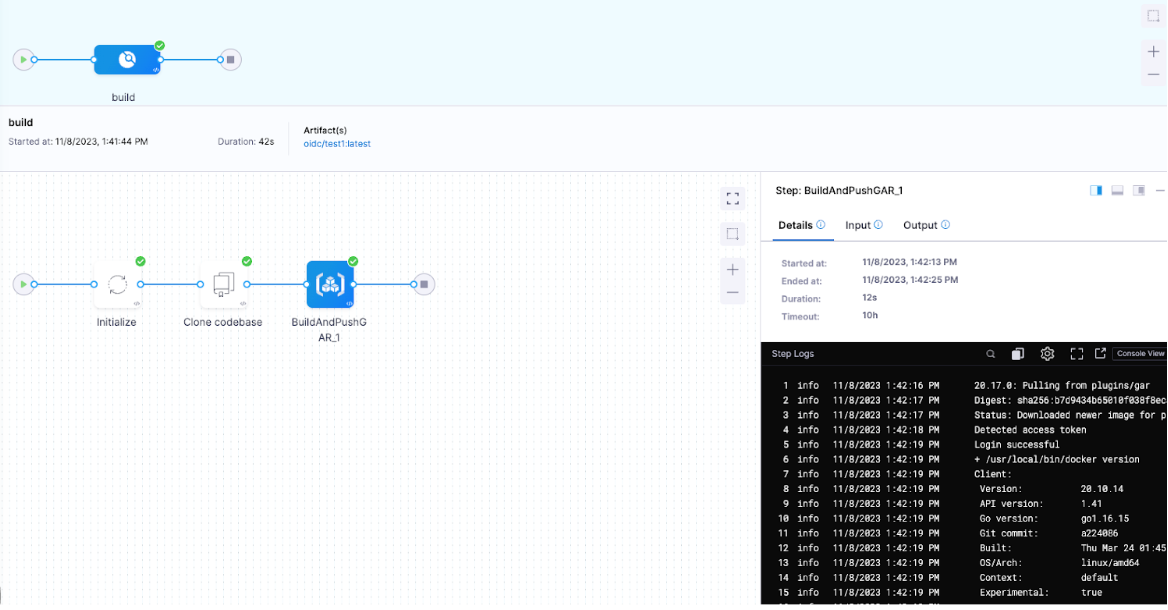
- Successful Deployment of Pipeline.
After configuring your settings, be sure to apply the changes and save them to Run. With a successful deployment, it is confirmed that the pipeline is running in an OIDC-enabled, secure environment.
Advantages of OpenID Connect (OIDC)
- Secure & Seamless Login – Provides strong authentication with Single Sign-On (SSO) support.
- Short-Term Tokens – Tokens have a TTL, reducing security risks in case of compromise.
- No Password Storage – Eliminates the need to store user credentials, reducing the risk of leaks and breaches.
- Standardized & Interoperable – Works across platforms and identity providers.
- Secure API Access – Uses short-lived access tokens instead of passwords, preventing unauthorized access.
- Regulatory Compliance – Aligns with GDPR, HIPAA, and other security standards.
Conclusion
In today's digital world, security and user convenience are more important than ever. OpenID Connect (OIDC) provides a powerful solution that simplifies authentication while ensuring secure access to applications. With OIDC, users can log in seamlessly without managing multiple passwords, and organizations can strengthen security and streamline user management.
As we’ve seen, OIDC not only verifies user identities but also manages their permissions, making it essential for modern applications. When integrated with platforms like Harness, OIDC enhances security in software deployments, allowing teams to focus on innovation instead of authentication challenges.
As digital identity continues to evolve, adopting OIDC will be key for businesses looking to provide a secure and user-friendly experience. Implementing OIDC ensures organizations are prepared for the demands of today’s digital landscape, paving the way for a more secure and efficient future.

